What is IDS in Networking? A Comprehensive Guide to Intrusion Detection Systems
In the complex and ever-evolving landscape of cybersecurity, understanding the tools and techniques used to protect networks is paramount. One such critical component is the Intrusion Detection System, or IDS. But what is IDS in networking, and why is it so important? This comprehensive guide will delve into the intricacies of IDS, exploring its definition, types, functionalities, and its role in maintaining a secure network environment.
Understanding Intrusion Detection Systems (IDS)
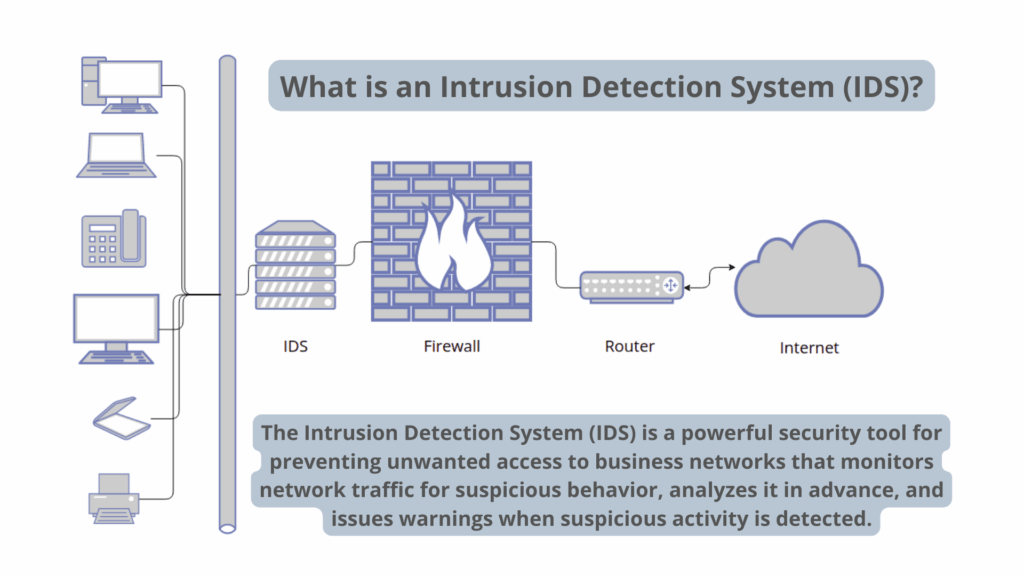
An Intrusion Detection System (IDS) is a security technology designed to monitor network traffic and system activities for malicious activities or policy violations. It acts as a surveillance system, identifying suspicious patterns that could indicate a security breach or an ongoing attack. Unlike firewalls, which primarily block unauthorized access, an IDS focuses on detection and alerting, providing valuable insights into potential threats that have bypassed initial security measures.
Essentially, an IDS is a detective, constantly scanning for unusual behavior and raising alarms when something suspicious is detected. This allows security teams to respond quickly and effectively to potential threats, minimizing the impact of security incidents.
Types of Intrusion Detection Systems
IDS solutions come in various forms, each designed to address specific aspects of network security. Understanding these different types is crucial for selecting the right IDS for your specific needs. Here are the primary types of IDS:
Network Intrusion Detection System (NIDS)
A Network Intrusion Detection System (NIDS) monitors network traffic for suspicious activity. It analyzes packets traversing the network, looking for patterns that match known attack signatures or deviations from normal network behavior. NIDS sensors are typically placed at strategic points within the network, such as at the perimeter or on critical network segments. The NIDS analyzes traffic in real-time, providing immediate alerts upon detection of potentially malicious activity. A key benefit of NIDS is its ability to monitor a large portion of the network with relatively few sensors. However, NIDS can be resource-intensive, requiring significant processing power to analyze network traffic effectively. Furthermore, encrypted traffic can pose a challenge for NIDS, as it cannot be easily inspected.
Host Intrusion Detection System (HIDS)
A Host Intrusion Detection System (HIDS) is installed on individual hosts or endpoints, such as servers or workstations. It monitors system logs, file integrity, and process activity on the host to detect suspicious behavior. HIDS provides a more granular level of security compared to NIDS, as it can detect attacks that target specific hosts. For example, a HIDS can detect unauthorized modifications to critical system files or the execution of malicious code. However, HIDS requires installation and maintenance on each host, which can be a significant overhead in large environments. Also, HIDS is only effective if the host itself is not compromised. If an attacker gains control of the host, they may be able to disable or circumvent the HIDS.
Signature-Based IDS
Signature-based IDS, also known as knowledge-based IDS, relies on a database of known attack signatures. When network traffic or system activity matches a signature in the database, the IDS generates an alert. This approach is highly effective at detecting known attacks, but it is less effective against new or unknown attacks, often referred to as zero-day exploits. The effectiveness of a signature-based IDS depends on the currency and comprehensiveness of its signature database. Regular updates are essential to ensure that the IDS can detect the latest threats. [See also: Understanding Zero-Day Exploits]
Anomaly-Based IDS
Anomaly-based IDS, also known as behavior-based IDS, establishes a baseline of normal network or system behavior. It then monitors for deviations from this baseline, flagging any activity that is significantly different as potentially malicious. This approach is more effective at detecting unknown attacks than signature-based IDS, as it does not rely on pre-existing signatures. However, anomaly-based IDS can generate a higher number of false positives, as legitimate activity may sometimes deviate from the established baseline. Careful configuration and tuning are required to minimize false positives and ensure that the IDS is accurately identifying malicious activity. This type of system often involves machine learning to understand normal behavior patterns. [See also: The Role of Machine Learning in Cybersecurity]
Hybrid IDS
A Hybrid IDS combines elements of both signature-based and anomaly-based detection techniques. This approach aims to leverage the strengths of both methods, providing a more comprehensive and accurate level of threat detection. By combining signature-based detection for known attacks with anomaly-based detection for unknown attacks, a hybrid IDS can offer a more robust defense against a wider range of threats. The key to a successful hybrid IDS is the effective integration of the different detection techniques and the ability to correlate alerts from multiple sources. [See also: Integrating Security Tools for Enhanced Threat Detection]
How an IDS Works: A Step-by-Step Overview
To fully understand what is IDS in networking, it’s helpful to examine the typical workflow of an IDS:
- Data Collection: The IDS collects data from various sources, such as network traffic, system logs, and application activity.
- Data Analysis: The collected data is analyzed using either signature-based or anomaly-based detection techniques (or a combination of both). Signature-based analysis compares the data against a database of known attack signatures. Anomaly-based analysis compares the data against a baseline of normal behavior.
- Alert Generation: If suspicious activity is detected, the IDS generates an alert. The alert typically includes information about the type of activity detected, the source and destination of the activity, and the severity of the threat.
- Reporting and Logging: The IDS logs all detected events and alerts, providing a record of security incidents. It also generates reports that summarize the security posture of the network or system.
- Response (Sometimes): Some advanced IDS systems, often referred to as Intrusion Prevention Systems (IPS), can take automated actions to respond to detected threats, such as blocking malicious traffic or terminating suspicious processes. However, most traditional IDS systems primarily focus on detection and alerting, leaving the response to security personnel.
The Difference Between IDS and IPS
While the terms IDS and IPS (Intrusion Prevention System) are often used interchangeably, they are distinct security technologies. The primary difference lies in their response capabilities. As mentioned earlier, an IDS primarily focuses on detecting and alerting, while an IPS goes a step further by taking automated actions to prevent attacks. [See also: IDS vs IPS: Key Differences and When to Use Each]
Here’s a table summarizing the key differences:
| Feature | IDS | IPS |
|---|---|---|
| Primary Function | Detection and Alerting | Detection and Prevention |
| Response | Alerts security personnel | Automated actions (e.g., blocking traffic) |
| Placement | Typically placed out-of-band (passively monitoring traffic) | Typically placed in-band (actively inspecting and controlling traffic) |
Benefits of Using an IDS
Implementing an IDS offers several significant benefits for network security:
- Early Threat Detection: IDS can detect malicious activity early in the attack lifecycle, allowing security teams to respond quickly and minimize the impact of security incidents.
- Improved Security Posture: By providing visibility into potential threats, IDS helps organizations improve their overall security posture.
- Compliance: Many regulations and standards require organizations to implement security controls, including intrusion detection systems.
- Forensic Analysis: IDS logs can be used for forensic analysis after a security incident, helping to determine the root cause of the incident and identify areas for improvement.
- Insider Threat Detection: An IDS can also detect malicious activity originating from within the organization, such as insider threats or compromised accounts.
Challenges of Using an IDS
While IDS offers numerous benefits, it’s important to be aware of the challenges associated with its implementation and management:
- False Positives: Anomaly-based IDS can generate a high number of false positives, requiring significant time and effort to investigate.
- False Negatives: IDS may fail to detect certain types of attacks, particularly new or sophisticated attacks.
- Encryption: Encrypted traffic can be difficult for IDS to analyze, potentially masking malicious activity.
- Performance Impact: IDS can consume significant processing power, potentially impacting network performance.
- Complexity: Configuring and managing an IDS can be complex, requiring specialized expertise.
Best Practices for Implementing an IDS
To maximize the effectiveness of an IDS, it’s important to follow these best practices:
- Define Clear Security Policies: Establish clear security policies that define acceptable network and system behavior.
- Choose the Right IDS: Select an IDS that is appropriate for your specific needs and environment. Consider factors such as network size, traffic volume, and security requirements.
- Proper Placement: Place IDS sensors strategically within the network to maximize coverage and effectiveness.
- Regular Updates: Keep the IDS software and signature database up to date to ensure that it can detect the latest threats.
- Tuning and Configuration: Carefully tune and configure the IDS to minimize false positives and optimize performance.
- Monitoring and Analysis: Regularly monitor IDS alerts and logs to identify and respond to security incidents.
- Integration with Other Security Tools: Integrate the IDS with other security tools, such as firewalls and SIEM (Security Information and Event Management) systems, to provide a more comprehensive security solution.
Conclusion: The Importance of IDS in Network Security
In conclusion, understanding what is IDS in networking is crucial for maintaining a robust security posture. While not a silver bullet, an IDS provides a critical layer of defense by detecting and alerting on malicious activity. By understanding the different types of IDS, their functionalities, and the challenges associated with their implementation, organizations can effectively leverage this technology to protect their networks and systems from evolving threats. An IDS, when properly implemented and managed, is an invaluable asset in the ongoing battle against cybercrime. The information provided here should give any network administrator or security professional a solid understanding of what is IDS in networking and how it can be beneficial.
