What is a Botnet? Understanding the Threat and How to Protect Yourself
In the digital age, where our lives are increasingly intertwined with the internet, understanding the various threats lurking online is crucial. One such threat, often operating silently and insidiously, is the botnet. But what is a botnet, exactly? In simple terms, a botnet is a network of computers infected with malware, allowing a hacker to control them remotely without the owners’ knowledge. These compromised computers, known as ‘bots’ or ‘zombies,’ can then be used to carry out a variety of malicious activities, from sending spam emails to launching large-scale cyberattacks.
This article will delve into the intricacies of what a botnet is, exploring how they are created, the dangers they pose, and, most importantly, how you can protect yourself from becoming a part of one. We’ll break down the technical jargon and provide practical advice to help you navigate the complex world of cybersecurity.
How Botnets Are Created
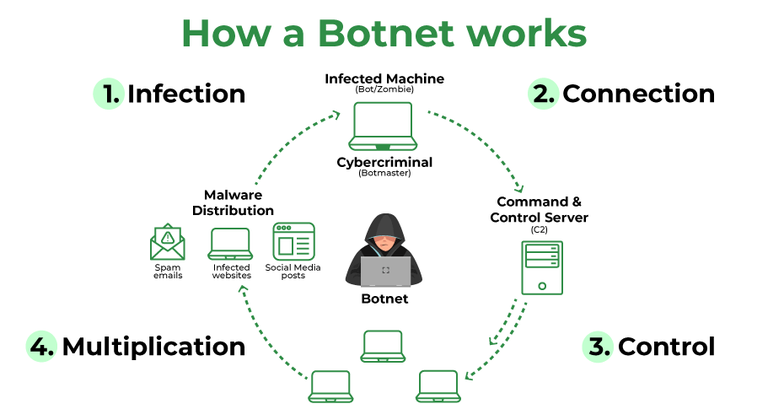
The creation of a botnet typically involves several stages. First, cybercriminals need to infect computers with malware. This can be achieved through various methods, including:
- Email attachments: Malicious files disguised as legitimate documents or images.
- Drive-by downloads: Exploiting vulnerabilities in websites to automatically download malware onto unsuspecting visitors’ computers.
- Software vulnerabilities: Taking advantage of security flaws in operating systems or applications.
- Infected software: Distributing malware through compromised software downloads.
Once a computer is infected, the malware allows the attacker to remotely control it. The infected computer then becomes a ‘bot,’ ready to carry out the attacker’s commands. The attacker, known as the ‘bot herder,’ can then control hundreds, thousands, or even millions of bots simultaneously, forming a botnet.
The Role of Malware
Malware is the key ingredient in creating a botnet. Different types of malware can be used, but some are more common than others. Trojans, for example, are often used to gain initial access to a computer. Once inside, they can download additional malware that allows the attacker to control the system. Viruses and worms can also be used to spread the infection to other computers, rapidly expanding the botnet.
Command and Control (C&C) Servers
The bot herder controls the botnet through a command and control (C&C) server. This server acts as the central hub, issuing instructions to the bots and receiving reports on their activities. C&C servers can be hosted on compromised servers or even on legitimate cloud services, making them difficult to track down and shut down. The communication between the bots and the C&C server is often encrypted to prevent detection.
The Dangers of Botnets
Botnets pose a significant threat to individuals, organizations, and even entire nations. Their ability to carry out large-scale attacks makes them a powerful weapon in the hands of cybercriminals. Some of the most common dangers associated with botnets include:
- Distributed Denial-of-Service (DDoS) attacks: Overwhelming a target server with traffic from thousands of bots, making it unavailable to legitimate users.
- Spam distribution: Sending massive amounts of spam emails, phishing scams, and malware-laden attachments.
- Data theft: Stealing sensitive information such as usernames, passwords, and financial data.
- Cryptocurrency mining: Using the processing power of infected computers to mine cryptocurrencies without the owners’ consent.
- Click fraud: Generating fraudulent clicks on online advertisements to inflate revenue for the attacker.
DDoS Attacks: A Common Botnet Application
DDoS attacks are one of the most visible and damaging consequences of botnet activity. By flooding a target server with traffic from thousands of bots, attackers can effectively shut down websites and online services. These attacks can be motivated by financial gain, political activism, or simply the desire to cause disruption. [See also: Understanding DDoS Attacks and Mitigation Strategies]
Spam and Phishing Campaigns
Botnets are also frequently used to distribute spam and phishing emails on a massive scale. Because the emails are sent from a large number of different IP addresses, it is difficult for email providers to block them all. This allows attackers to reach a wider audience and increase the chances of successfully phishing for sensitive information or spreading malware.
How to Protect Yourself from Botnets
Protecting yourself from botnets requires a multi-layered approach that includes both technical and behavioral measures. Here are some essential steps you can take:
- Keep your software up to date: Regularly update your operating system, web browser, and other software to patch security vulnerabilities.
- Use a reputable antivirus program: Install a reliable antivirus program and keep it up to date. Schedule regular scans to detect and remove malware.
- Be cautious of suspicious emails: Avoid clicking on links or opening attachments from unknown senders.
- Use strong passwords: Use strong, unique passwords for all your online accounts. Consider using a password manager to help you generate and store your passwords.
- Enable a firewall: A firewall can help prevent unauthorized access to your computer.
- Be careful when downloading software: Only download software from trusted sources. Be wary of free software or browser extensions that seem too good to be true.
- Use a VPN: A Virtual Private Network (VPN) can encrypt your internet traffic and protect your privacy.
- Educate yourself: Stay informed about the latest cybersecurity threats and best practices.
The Importance of Software Updates
Software updates are crucial for protecting yourself from botnets because they often include patches for security vulnerabilities. Cybercriminals are constantly looking for new vulnerabilities to exploit, so it’s essential to keep your software up to date to close these loopholes. [See also: The Importance of Regular Software Updates for Cybersecurity]
Choosing the Right Antivirus Program
A reputable antivirus program can help detect and remove malware before it can infect your computer. When choosing an antivirus program, look for one that offers real-time protection, automatic updates, and a comprehensive scanning engine. Free antivirus programs may offer basic protection, but they often lack the advanced features and support of paid programs. Ensuring your devices are secure is key to avoiding becoming part of a botnet.
Detecting a Botnet Infection
Even with the best security measures in place, it’s still possible to become infected with malware and become part of a botnet. Here are some signs that your computer may be infected:
- Slow performance: Your computer may run slower than usual, especially when performing simple tasks.
- High CPU usage: Your CPU usage may be consistently high, even when you’re not running any demanding applications.
- Unexpected pop-ups: You may see unexpected pop-up ads or error messages.
- Unusual network activity: Your computer may be sending or receiving a lot of network traffic, even when you’re not using the internet.
- Changes to your browser settings: Your browser homepage or search engine may have been changed without your knowledge.
If you suspect that your computer is infected, run a full scan with your antivirus program. You may also want to consider using a second opinion scanner, which is a free tool that can detect malware that your primary antivirus program may have missed. If the scan detects malware, follow the instructions to remove it. You should also change your passwords for all your online accounts.
The Future of Botnets
Botnets are constantly evolving, and cybercriminals are always finding new ways to create and use them. As the Internet of Things (IoT) becomes more prevalent, the number of potential bots is growing exponentially. IoT devices, such as smart TVs, security cameras, and even refrigerators, are often poorly secured and can be easily infected with malware. This makes them attractive targets for bot herders. The fight against botnets is an ongoing battle, and it requires constant vigilance and adaptation.
The Rise of IoT Botnets
The rise of IoT devices has created a new frontier for botnets. These devices are often left unprotected, making them easy targets for cybercriminals. IoT botnets can be used to launch DDoS attacks, mine cryptocurrencies, or even spy on users. [See also: Securing Your IoT Devices: A Comprehensive Guide]
The Role of Artificial Intelligence (AI)
Artificial intelligence (AI) is also playing an increasingly important role in the world of botnets. AI can be used to automate the process of creating and managing botnets, making them more efficient and difficult to detect. AI can also be used to develop more sophisticated malware that can evade detection by traditional antivirus programs. However, AI can also be used to defend against botnets by detecting and blocking malicious traffic. The use of AI in cybersecurity is a double-edged sword.
Conclusion
What is a botnet? It’s a complex and evolving threat that requires constant vigilance. By understanding how botnets are created, the dangers they pose, and how to protect yourself, you can significantly reduce your risk of becoming a victim. Remember to keep your software up to date, use a reputable antivirus program, be cautious of suspicious emails, and educate yourself about the latest cybersecurity threats. The fight against botnets is a shared responsibility, and by working together, we can make the internet a safer place for everyone. Staying informed and proactive is the best defense against these insidious networks. Understanding what a botnet can do is crucial for anyone using the internet today. The constant evolution of these threats means ongoing education and adaptation are essential to maintaining online safety and security. By taking preventative measures and staying informed, you can minimize your risk of becoming part of a botnet and contribute to a safer online environment. The key takeaway is that awareness and proactive security practices are your best defenses against botnet threats. Remember, what a botnet is and how it operates is the first step in protecting yourself and your devices.
