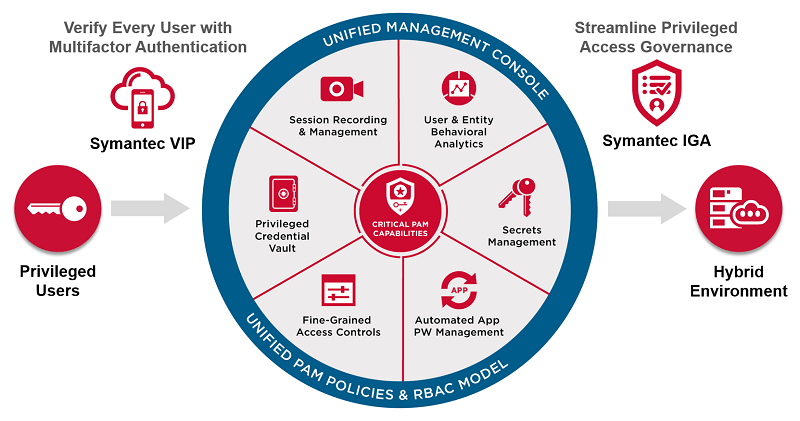
Top Privileged Access Management Companies: A Comprehensive Guide
In today’s complex cybersecurity landscape, protecting privileged accounts is paramount. These accounts, which possess elevated access rights, are prime targets for malicious actors seeking to infiltrate systems, steal sensitive data, and disrupt operations. Privileged access management (PAM) solutions are designed to mitigate these risks by controlling, monitoring, and auditing privileged access. Choosing the right privileged access management companies is crucial for organizations of all sizes. This guide provides a comprehensive overview of leading privileged access management companies, their offerings, and key considerations for selecting the best solution for your organization.
Understanding Privileged Access Management
Before diving into specific privileged access management companies, it’s essential to understand the core principles of PAM. Privileged access management encompasses a range of strategies and technologies aimed at securing privileged accounts and preventing their misuse. Key components of a robust PAM program include:
- Privilege Discovery: Identifying and cataloging all privileged accounts within the organization.
- Vaulting: Securely storing and managing privileged credentials, such as passwords and SSH keys.
- Access Control: Granting users the minimum level of privilege necessary to perform their tasks.
- Session Management: Monitoring and recording privileged sessions to detect suspicious activity.
- Auditing and Reporting: Generating comprehensive audit trails of privileged access activities.
Key Considerations When Choosing a PAM Solution
Selecting the right privileged access management solution requires careful consideration of your organization’s specific needs and risk profile. Here are some key factors to consider:
- Scalability: The solution should be able to scale to accommodate your organization’s growing needs.
- Integration: The solution should integrate seamlessly with your existing IT infrastructure and security tools.
- Ease of Use: The solution should be user-friendly and easy to manage.
- Compliance: The solution should help you meet relevant regulatory compliance requirements.
- Deployment Options: Consider cloud-based, on-premise, or hybrid deployment options based on your organizational strategy.
- Vendor Reputation and Support: Research the vendor’s reputation and ensure they provide adequate support.
Leading Privileged Access Management Companies
The privileged access management market is populated by a variety of vendors, each offering unique strengths and capabilities. Here’s a look at some of the leading privileged access management companies:
CyberArk
CyberArk is widely recognized as a leader in the privileged access management space. Their comprehensive platform offers a wide range of features, including:
- Privileged Access Security
- Endpoint Privilege Manager
- Cloud Entitlements Manager
- Secrets Management
CyberArk’s solutions are known for their robust security features and scalability, making them a popular choice for large enterprises. Their focus on innovation also keeps them at the forefront of the industry, addressing emerging threats and adapting to evolving compliance landscapes. However, the complexity and cost of CyberArk’s solutions can be a barrier for smaller organizations.
BeyondTrust
BeyondTrust offers a unified platform for privileged access management, vulnerability management, and identity management. Their offerings include:
- Password Safe
- Privilege Management for Windows and Mac
- Endpoint Privilege Management
- Secure Remote Access
BeyondTrust is known for its user-friendly interface and comprehensive feature set. Their unified platform approach simplifies management and provides a holistic view of security risks. They also offer strong endpoint privilege management capabilities, which are essential for protecting against malware and insider threats. BeyondTrust is often considered a strong contender for organizations seeking a balance between functionality and ease of use.
ThycoticCentrify
ThycoticCentrify was formed by the merger of Thycotic and Centrify, creating a powerful force in the privileged access management market. Their combined portfolio offers a wide range of solutions, including:
- Secret Server
- Privilege Manager
- Cloud Access Manager
- DirectControl
ThycoticCentrify aims to provide a comprehensive and integrated approach to PAM, covering on-premises, cloud, and hybrid environments. Their solutions are designed to be easy to deploy and manage, making them a good option for organizations with limited IT resources. The merger of Thycotic and Centrify has expanded their capabilities and market reach, positioning them as a significant player in the PAM industry. [See also: Cloud Security Best Practices]
One Identity
One Identity offers a range of identity and access management (IAM) solutions, including privileged access management capabilities. Their PAM offerings include:
- Safeguard
- Password Manager
- Active Roles
One Identity’s PAM solutions are designed to integrate with their broader IAM platform, providing a unified approach to identity governance and access control. This integration can simplify management and improve security posture. Their Safeguard solution is particularly well-regarded for its robust session management and auditing capabilities. One Identity is a strong choice for organizations seeking a comprehensive IAM solution with integrated PAM functionality.
ManageEngine
ManageEngine, a division of Zoho Corporation, offers a suite of IT management software, including privileged access management solutions. Their PAM offerings include:
- Password Manager Pro
- PAM360
ManageEngine’s PAM solutions are known for their affordability and ease of use, making them a popular choice for small and medium-sized businesses (SMBs). Their Password Manager Pro solution provides essential PAM functionality, such as password vaulting and access control. Their PAM360 solution offers a more comprehensive set of features, including session management and auditing. ManageEngine is a solid option for organizations seeking a cost-effective and easy-to-manage PAM solution.
The Future of Privileged Access Management
The privileged access management landscape is constantly evolving, driven by emerging threats and technological advancements. Some key trends shaping the future of PAM include:
- Cloud-Native PAM: As more organizations migrate to the cloud, there is a growing demand for PAM solutions that are specifically designed for cloud environments.
- DevSecOps Integration: Integrating PAM into the DevOps pipeline is becoming increasingly important to secure the software development lifecycle.
- AI and Machine Learning: AI and machine learning are being used to automate PAM tasks, such as anomaly detection and risk assessment.
- Passwordless Authentication: The move towards passwordless authentication is reducing the reliance on passwords and mitigating the risk of password-related attacks.
Conclusion
Choosing the right privileged access management companies is a critical decision that can significantly impact your organization’s security posture. By carefully considering your specific needs, evaluating different vendor offerings, and staying abreast of emerging trends, you can select a PAM solution that effectively protects your privileged accounts and mitigates the risk of cyberattacks. Remember to prioritize solutions that offer scalability, integration capabilities, ease of use, and strong vendor support. Investing in a robust privileged access management strategy is an investment in the long-term security and resilience of your organization. The landscape of privileged access management is complex, but understanding the key players and their offerings will empower you to make an informed decision. Always ensure compliance with relevant regulations and tailor the solution to your specific IT environment. Properly implemented, PAM can dramatically reduce the risk of breaches stemming from compromised privileged credentials. [See also: Cybersecurity Trends 2024]
