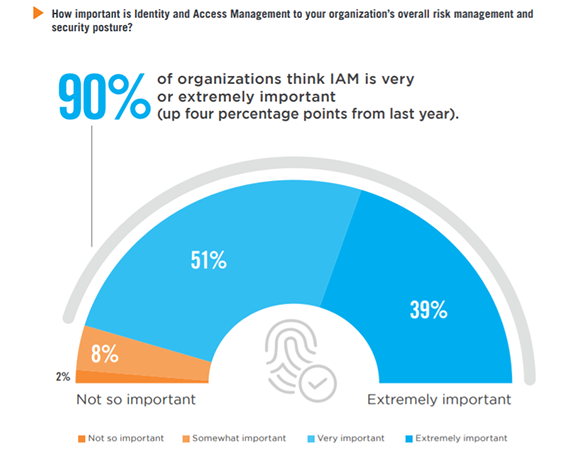
The Paramount Importance of Identity and Access Management (IAM)
In today’s interconnected digital landscape, the **importance of IAM** (Identity and Access Management) cannot be overstated. It’s no longer merely a technical consideration but a fundamental business imperative. From securing sensitive data to ensuring regulatory compliance and enhancing operational efficiency, a robust IAM framework is crucial for organizations of all sizes. This article delves into the multifaceted **importance of IAM**, exploring its key benefits, core components, and best practices for implementation.
Understanding Identity and Access Management (IAM)
At its core, IAM is a framework of policies and technologies designed to ensure that the right individuals (identities) have the appropriate access to the right resources (systems, applications, data) at the right time and for the right reasons. It’s about managing digital identities and controlling their access privileges across an organization’s IT infrastructure. The **importance of IAM** stems from its ability to mitigate risks associated with unauthorized access, data breaches, and compliance violations.
Key Benefits Highlighting the Importance of IAM
The **importance of IAM** is underscored by the numerous benefits it provides to organizations:
- Enhanced Security: IAM minimizes the risk of unauthorized access and data breaches by enforcing strong authentication, authorization, and access control policies. This protects sensitive data and critical systems from malicious actors.
- Improved Compliance: Many industries are subject to strict regulatory requirements regarding data privacy and security. IAM helps organizations meet these compliance mandates by providing auditable access controls and ensuring that data is accessed only by authorized personnel.
- Increased Operational Efficiency: By automating access provisioning and de-provisioning processes, IAM reduces the administrative burden on IT staff and improves operational efficiency. This allows IT teams to focus on more strategic initiatives.
- Reduced Costs: IAM can help organizations reduce costs by streamlining access management processes, minimizing the risk of data breaches, and improving compliance.
- Enhanced User Experience: IAM can improve the user experience by providing seamless access to the resources they need, without compromising security. Single sign-on (SSO) is a prime example of this.
- Improved Visibility and Control: IAM provides a centralized view of all user identities and access privileges, allowing organizations to monitor and control access to sensitive data and critical systems.
Core Components of an IAM System
A comprehensive IAM system typically comprises several key components:
- Identity Management: This involves creating, managing, and maintaining user identities throughout their lifecycle. This includes onboarding new users, updating user information, and de-provisioning users when they leave the organization.
- Access Management: This focuses on controlling access to resources based on user roles, attributes, and context. This includes authentication, authorization, and access control policies.
- Authentication: This is the process of verifying a user’s identity. Common authentication methods include passwords, multi-factor authentication (MFA), and biometrics.
- Authorization: This is the process of determining what resources a user is allowed to access after they have been authenticated.
- Access Control: This involves enforcing access policies and ensuring that users only have access to the resources they are authorized to use. Role-Based Access Control (RBAC) is a common approach.
- Privileged Access Management (PAM): This focuses on managing access to privileged accounts, such as administrator accounts, which have elevated privileges. PAM is crucial for protecting critical systems and data from insider threats.
- Single Sign-On (SSO): This allows users to access multiple applications with a single set of credentials, improving the user experience and reducing password fatigue.
- Multi-Factor Authentication (MFA): This requires users to provide two or more factors of authentication to verify their identity, significantly enhancing security.
- Identity Governance and Administration (IGA): This provides a framework for managing user identities and access privileges in a compliant and auditable manner.
Implementing an Effective IAM Strategy
Implementing an effective IAM strategy requires careful planning and execution. Here are some best practices to consider:
- Define Clear Goals and Objectives: Before implementing an IAM system, it’s important to define clear goals and objectives. What are you trying to achieve with IAM? What problems are you trying to solve?
- Assess Your Current IAM Landscape: Conduct a thorough assessment of your current IAM landscape to identify gaps and areas for improvement.
- Develop a Comprehensive IAM Strategy: Develop a comprehensive IAM strategy that aligns with your business goals and objectives. This strategy should outline your IAM vision, goals, objectives, and roadmap.
- Choose the Right IAM Solution: Select an IAM solution that meets your specific needs and requirements. Consider factors such as scalability, flexibility, integration capabilities, and cost.
- Implement Strong Authentication and Authorization Policies: Implement strong authentication and authorization policies to ensure that only authorized users have access to sensitive data and critical systems.
- Automate Access Provisioning and De-provisioning: Automate access provisioning and de-provisioning processes to reduce the administrative burden on IT staff and improve operational efficiency.
- Monitor and Audit Access Activity: Monitor and audit access activity to detect and prevent unauthorized access.
- Provide User Training: Provide user training on IAM policies and procedures to ensure that users understand their responsibilities and how to use the IAM system.
- Regularly Review and Update Your IAM Strategy: Regularly review and update your IAM strategy to ensure that it remains aligned with your business goals and objectives.
The Future of IAM
The field of IAM is constantly evolving to address new challenges and opportunities. Some of the key trends shaping the future of IAM include:
- Cloud-Based IAM: Cloud-based IAM solutions are becoming increasingly popular due to their scalability, flexibility, and cost-effectiveness.
- Identity as a Service (IDaaS): IDaaS solutions provide a comprehensive suite of IAM capabilities as a managed service.
- Zero Trust Security: Zero trust security is a security model that assumes that no user or device should be trusted by default, regardless of whether they are inside or outside the organization’s network. IAM plays a critical role in implementing zero trust security.
- Biometric Authentication: Biometric authentication methods, such as fingerprint scanning and facial recognition, are becoming increasingly common.
- Decentralized Identity: Decentralized identity is a new approach to identity management that gives individuals more control over their digital identities.
The Critical Importance of IAM in Modern Organizations
In conclusion, the **importance of IAM** is undeniable in today’s complex and interconnected digital world. A well-designed and implemented IAM strategy is essential for protecting sensitive data, ensuring regulatory compliance, enhancing operational efficiency, and improving the user experience. By understanding the key benefits, core components, and best practices of IAM, organizations can effectively manage digital identities and control access privileges, ultimately mitigating risks and achieving their business objectives. The **importance of IAM** only grows as data security threats become more sophisticated and regulatory landscapes become more complex. Investing in a robust IAM solution is an investment in the future security and success of your organization. The **importance of IAM** is not just about technology; it’s about people, processes, and policies working together to create a secure and efficient environment. Understanding the **importance of IAM** is the first step towards building a strong security posture. Recognizing the **importance of IAM** allows organizations to prioritize resources and focus on implementing effective security measures. Don’t underestimate the **importance of IAM**; it’s a critical component of any modern security strategy. The **importance of IAM** extends beyond IT; it’s a business imperative that impacts all aspects of an organization. Therefore, acknowledging the **importance of IAM** is crucial for long-term success. Finally, remember the **importance of IAM** is not a one-time project, but an ongoing process that requires continuous monitoring and improvement.
[See also: Understanding Zero Trust Security]
[See also: Best Practices for Multi-Factor Authentication]
[See also: The Role of IAM in Cloud Security]
