Securing the Digital Frontier: Choosing the Right Identity Access Management Solution
In today’s interconnected world, where data breaches are commonplace and cyber threats loom large, organizations need robust defenses to protect sensitive information. At the forefront of these defenses lies Identity Access Management (IAM), a critical framework for controlling who has access to what within an organization’s digital ecosystem. Selecting the right identity access management solution is no longer a luxury but a necessity for businesses of all sizes. This article delves into the importance of IAM, explores the key features to look for in an identity access management solution, and provides a roadmap for choosing the right fit for your organization.
Understanding Identity Access Management (IAM)
IAM is more than just a password management system; it’s a comprehensive framework that governs how users are identified, authenticated, and authorized to access resources. It encompasses policies, processes, and technologies that ensure only authorized individuals can access specific data and applications. Think of it as the gatekeeper of your digital kingdom, ensuring that only those with the proper credentials can enter and access valuable assets. A properly implemented identity access management solution can drastically reduce the risk of unauthorized access and data breaches.
The Core Components of IAM
- Identification: Verifying the identity of a user or device attempting to access a system.
- Authentication: Confirming the identity of a user or device, often through passwords, multi-factor authentication (MFA), or biometric scans.
- Authorization: Granting or denying access to specific resources based on the user’s role, permissions, and privileges.
- Access Governance: Managing and controlling user access rights, ensuring compliance with regulations and internal policies.
- Auditing: Tracking user activity and access attempts to identify potential security threats and ensure accountability.
Why is an Identity Access Management Solution Crucial?
The benefits of implementing an identity access management solution are multifaceted and far-reaching. Beyond simply preventing unauthorized access, IAM plays a vital role in enhancing security posture, streamlining operations, and ensuring regulatory compliance.
Enhanced Security
A strong IAM system acts as a crucial line of defense against cyber threats. By controlling who has access to what, it minimizes the risk of insider threats, data breaches, and unauthorized access to sensitive information. Multi-factor authentication (MFA), a key component of many identity access management solution offerings, adds an extra layer of security by requiring users to provide multiple forms of verification before granting access. [See also: The Importance of Multi-Factor Authentication]
Improved Compliance
Many industries are subject to strict regulations regarding data privacy and security, such as GDPR, HIPAA, and PCI DSS. An identity access management solution can help organizations meet these compliance requirements by providing tools for managing user access, tracking activity, and generating audit reports. By implementing a robust IAM system, organizations can demonstrate their commitment to data protection and avoid costly penalties for non-compliance.
Streamlined Operations
IAM can automate many of the manual processes associated with user provisioning, deprovisioning, and access management. This frees up IT staff to focus on more strategic initiatives and reduces the risk of human error. Self-service portals allow users to manage their own passwords and access requests, further streamlining operations and improving user experience. An effective identity access management solution enhances efficiency and reduces administrative overhead.
Reduced Costs
While implementing an IAM system requires an initial investment, the long-term cost savings can be significant. By automating access management processes, organizations can reduce IT costs, minimize the risk of data breaches (which can be incredibly expensive), and improve employee productivity. Furthermore, a well-designed identity access management solution can scale to meet the evolving needs of the organization, avoiding the need for costly upgrades or replacements in the future.
Key Features to Look for in an Identity Access Management Solution
Not all identity access management solutions are created equal. When evaluating different options, it’s crucial to consider the specific needs of your organization and look for features that align with your security requirements, compliance obligations, and operational goals.
Single Sign-On (SSO)
SSO allows users to access multiple applications and systems with a single set of credentials. This simplifies the login process, improves user experience, and reduces the risk of password fatigue. An identity access management solution with SSO capabilities can significantly enhance security and productivity. [See also: Benefits of Single Sign-On for Enterprise Security]
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password, a code sent to their phone, or a biometric scan. This makes it much more difficult for attackers to gain unauthorized access to systems and data. Implementing MFA through your identity access management solution is a crucial step in protecting against phishing attacks and other common security threats.
Role-Based Access Control (RBAC)
RBAC allows you to grant access to resources based on a user’s role within the organization. This simplifies access management, ensures that users only have access to the resources they need, and reduces the risk of unauthorized access. A well-implemented RBAC system, integrated with your identity access management solution, is essential for maintaining a secure and compliant environment.
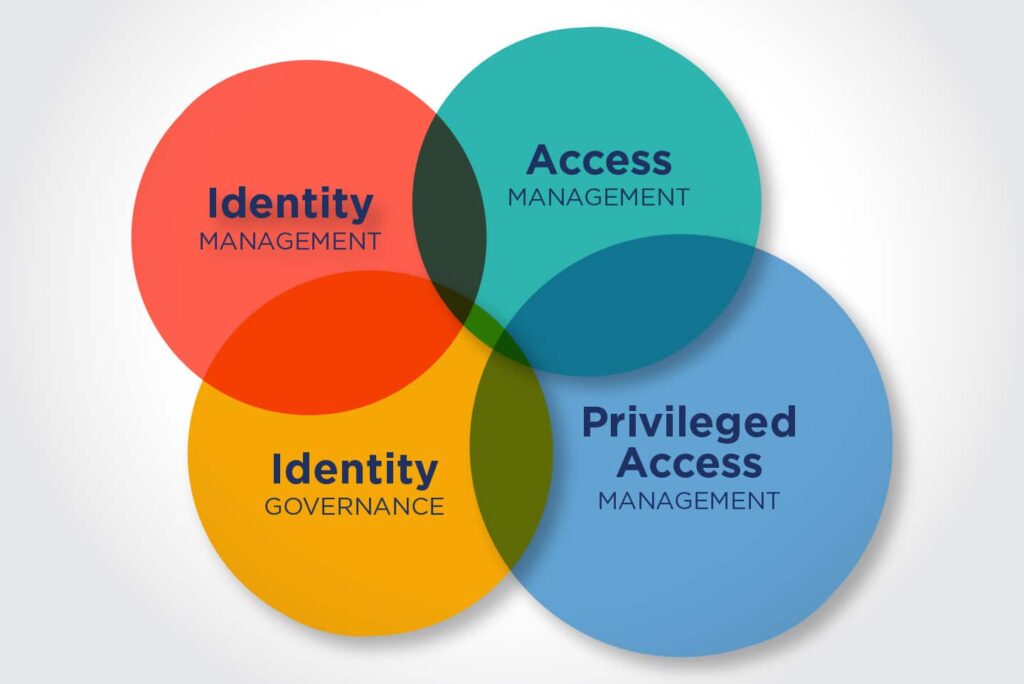
Privileged Access Management (PAM)
PAM focuses on managing and controlling access to privileged accounts, such as those used by system administrators and developers. These accounts have elevated privileges and can pose a significant security risk if compromised. An identity access management solution with PAM capabilities can help organizations secure privileged accounts, monitor activity, and prevent unauthorized access to sensitive systems. [See also: Understanding Privileged Access Management]
Identity Governance and Administration (IGA)
IGA provides a centralized platform for managing user identities, access rights, and compliance policies. This includes features such as user provisioning, deprovisioning, access certification, and audit reporting. An identity access management solution with IGA capabilities can help organizations automate access management processes, enforce security policies, and ensure compliance with regulations.
Cloud Integration
In today’s cloud-centric world, it’s essential to choose an identity access management solution that integrates seamlessly with cloud applications and services. This allows you to extend your security policies and access controls to the cloud, ensuring that your data is protected regardless of where it resides. Look for a solution that supports common cloud standards such as SAML and OAuth.
Choosing the Right Identity Access Management Solution: A Roadmap
Selecting the right identity access management solution can be a complex process. Here’s a roadmap to guide you through the decision-making process:
- Assess Your Needs: Identify your specific security requirements, compliance obligations, and operational goals. What are your biggest security concerns? What regulations do you need to comply with? What are your current access management challenges?
- Define Your Budget: Determine how much you’re willing to invest in an IAM solution. Consider both the initial cost of implementation and the ongoing maintenance and support costs.
- Research Different Solutions: Explore different identity access management solution providers and compare their features, pricing, and customer reviews. Look for a solution that aligns with your needs and budget.
- Request a Demo: Schedule a demo with the vendors you’re considering to see the solution in action and ask questions. This is a great opportunity to evaluate the user interface, features, and overall functionality of the solution.
- Conduct a Pilot Program: Before rolling out the solution to your entire organization, conduct a pilot program with a small group of users. This will allow you to identify any potential issues and fine-tune the configuration before a full-scale deployment.
- Implement and Configure: Work with the vendor to implement and configure the solution according to your specific needs. This may involve integrating with existing systems, setting up user roles and permissions, and configuring authentication policies.
- Train Your Users: Provide training to your users on how to use the new IAM system. This will help them understand the benefits of the solution and ensure that they can use it effectively.
- Monitor and Maintain: Continuously monitor the performance of the IAM system and make adjustments as needed. This will help you ensure that the solution is meeting your security requirements and operational goals. Regular audits and security assessments are crucial.
The Future of Identity Access Management
The field of IAM is constantly evolving to meet the ever-changing threat landscape. Emerging trends such as passwordless authentication, behavioral biometrics, and AI-powered security are shaping the future of identity access management solution offerings. As organizations continue to embrace digital transformation, the importance of IAM will only continue to grow.
Conclusion
In conclusion, choosing the right identity access management solution is a critical investment for any organization looking to protect its data, streamline operations, and ensure regulatory compliance. By carefully assessing your needs, researching different solutions, and following the roadmap outlined in this article, you can select an IAM system that meets your specific requirements and helps you secure your digital frontier. The right identity access management solution is not just a tool; it’s a strategic asset that can help you achieve your business goals while mitigating risk.
