Navigating the Landscape: A Comprehensive Guide to Threat Intelligence Products
In today’s digital age, businesses face an ever-increasing barrage of cyber threats. Protecting sensitive data and maintaining operational integrity requires a proactive approach, and that’s where threat intelligence products come into play. These tools provide organizations with the insights necessary to understand, anticipate, and mitigate potential cyberattacks. This article will delve into the world of threat intelligence products, exploring their benefits, key features, and how to choose the right solution for your specific needs.
Understanding Threat Intelligence
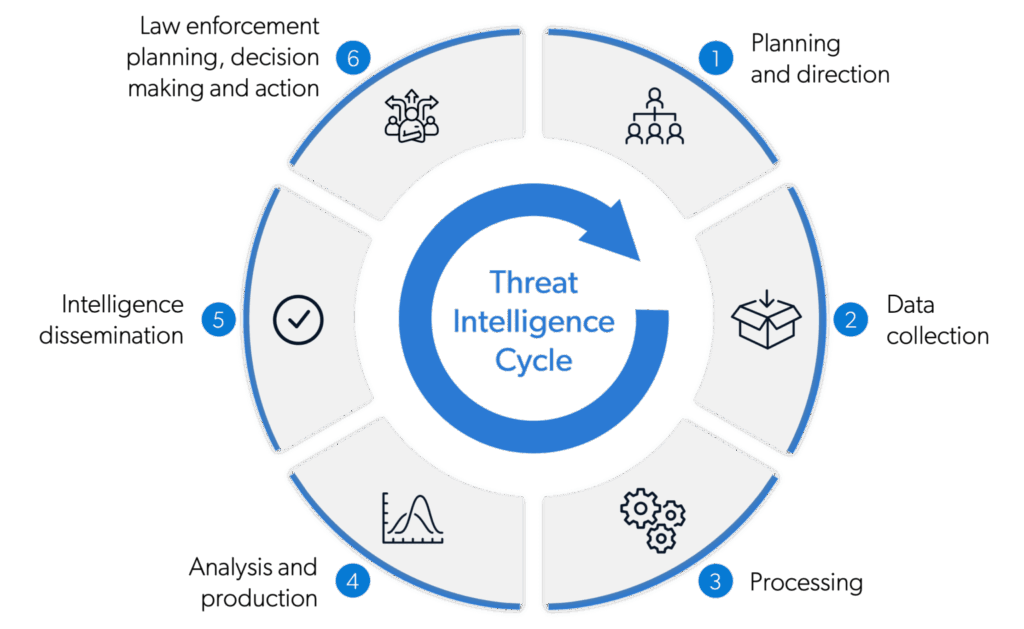
Before diving into the specifics of threat intelligence products, it’s crucial to understand the fundamental concept of threat intelligence itself. Threat intelligence is more than just data; it’s information that has been analyzed, refined, and contextualized to provide actionable insights. It answers critical questions like:
- Who are the attackers targeting my organization?
- What tactics, techniques, and procedures (TTPs) are they using?
- What vulnerabilities are they exploiting?
- How can I proactively defend against these threats?
By leveraging threat intelligence products, organizations can move beyond reactive security measures and adopt a proactive stance, anticipating and preventing attacks before they cause significant damage. This approach helps in reducing the attack surface and minimizing the impact of successful breaches.
The Benefits of Threat Intelligence Products
Implementing threat intelligence products offers a range of benefits, including:
- Proactive Security: Enables organizations to anticipate and prevent attacks before they occur.
- Improved Threat Detection: Enhances the ability to identify and respond to threats quickly and effectively.
- Reduced Risk: Minimizes the potential impact of cyberattacks on business operations and reputation.
- Enhanced Incident Response: Provides valuable context and insights to facilitate faster and more effective incident response.
- Better Resource Allocation: Helps organizations prioritize security efforts and allocate resources effectively.
- Informed Decision-Making: Provides actionable intelligence to inform security strategies and decision-making processes.
Key Features of Threat Intelligence Products
Threat intelligence products vary in their capabilities, but some key features are common across most solutions:
- Threat Feeds: Real-time streams of information about emerging threats, vulnerabilities, and malicious actors.
- Vulnerability Intelligence: Information about known vulnerabilities and exploits, helping organizations prioritize patching efforts.
- Malware Analysis: Analysis of malware samples to identify their characteristics and behavior.
- Reputation Intelligence: Information about the reputation of IP addresses, domains, and other online entities, helping organizations identify potentially malicious sources.
- Dark Web Monitoring: Monitoring of dark web forums and marketplaces for stolen data and other illicit activities.
- Threat Actor Profiling: Detailed profiles of known threat actors, including their motivations, TTPs, and targets.
- Integration with Security Tools: Integration with other security tools, such as SIEMs, firewalls, and intrusion detection systems, to automate threat detection and response.
- Customizable Reporting: Ability to generate customized reports to track key metrics and communicate threat intelligence insights to stakeholders.
Types of Threat Intelligence Products
The market offers various types of threat intelligence products, each catering to different needs and requirements:
- Threat Intelligence Platforms (TIPs): Centralized platforms for collecting, analyzing, and sharing threat intelligence data.
- Security Information and Event Management (SIEM) Systems: Systems that collect and analyze security logs and events to identify and respond to threats. Many SIEM solutions now incorporate threat intelligence feeds.
- Threat Feed Subscriptions: Subscriptions to specific threat intelligence feeds that provide real-time information about emerging threats.
- Vulnerability Management Tools: Tools that help organizations identify and prioritize vulnerabilities in their systems and applications.
- Endpoint Detection and Response (EDR) Solutions: Solutions that monitor endpoints for malicious activity and provide tools for incident response.
Choosing the Right Threat Intelligence Product
Selecting the right threat intelligence product can be a daunting task, given the variety of options available. Consider the following factors when making your decision:
- Your Organization’s Needs: What are your specific threat intelligence requirements? What types of threats are you most concerned about? What resources do you have available to manage and analyze threat intelligence data?
- Data Quality: How reliable and accurate is the threat intelligence data provided by the product? Does the vendor have a strong reputation for data quality?
- Integration Capabilities: Does the product integrate with your existing security tools and infrastructure? Can it share threat intelligence data with other systems?
- Usability: Is the product easy to use and manage? Does it provide a user-friendly interface and clear documentation?
- Scalability: Can the product scale to meet your organization’s growing needs? Can it handle increasing volumes of threat intelligence data?
- Vendor Reputation: What is the vendor’s reputation in the industry? Do they have a track record of providing reliable and effective threat intelligence products?
- Pricing: What is the cost of the product? Does the pricing model align with your budget and usage patterns?
Implementing Threat Intelligence Products
Once you’ve selected a threat intelligence product, it’s essential to implement it effectively. Here are some best practices:
- Define Clear Objectives: What do you hope to achieve with your threat intelligence program? Define specific, measurable, achievable, relevant, and time-bound (SMART) goals.
- Establish a Threat Intelligence Team: Assemble a team of security professionals who are responsible for managing and analyzing threat intelligence data.
- Develop a Threat Intelligence Process: Define a clear process for collecting, analyzing, and sharing threat intelligence data.
- Integrate Threat Intelligence with Security Operations: Integrate threat intelligence data with your security operations center (SOC) to improve threat detection and response.
- Train Your Staff: Provide training to your staff on how to use threat intelligence data to improve security awareness and decision-making.
- Regularly Evaluate and Improve: Regularly evaluate the effectiveness of your threat intelligence program and make adjustments as needed.
The Future of Threat Intelligence Products
The field of threat intelligence products is constantly evolving, driven by the ever-changing threat landscape. Future trends include:
- Increased Automation: Greater automation of threat intelligence collection, analysis, and dissemination.
- Artificial Intelligence and Machine Learning: Increased use of AI and ML to improve threat detection and prediction.
- Enhanced Collaboration: Greater collaboration between organizations to share threat intelligence data.
- Focus on Actionable Intelligence: Emphasis on providing actionable intelligence that can be readily used to improve security.
- Integration with Cloud Security: Tighter integration with cloud security solutions to protect cloud-based assets.
Conclusion
Threat intelligence products are an essential component of any modern cybersecurity strategy. By providing organizations with the insights they need to understand, anticipate, and mitigate cyber threats, these tools can significantly reduce risk and improve security posture. By carefully evaluating your organization’s needs and selecting the right threat intelligence product, you can empower your security team to proactively defend against the ever-evolving threat landscape.
Investing in robust threat intelligence products and developing a strong threat intelligence program is a critical step towards building a more resilient and secure organization. Don’t wait for the next attack; take proactive steps today to protect your valuable assets and data.
[See also: Cybersecurity Best Practices]
[See also: Data Breach Prevention]
[See also: Network Security Solutions]
