Man-in-the-Middle (MITM) Attacks: Understanding, Preventing, and Mitigating
In today’s interconnected digital landscape, cybersecurity threats are becoming increasingly sophisticated. One of the most insidious and potentially damaging is the Man-in-the-Middle (MITM) attack. This article provides a comprehensive overview of MITM attacks, exploring their mechanisms, potential consequences, and effective strategies for prevention and mitigation. Understanding MITM attacks is crucial for individuals and organizations alike to protect sensitive data and maintain secure communications. The goal is to provide clarity on what a man in the middle attack is, how it operates, and what steps to take to prevent becoming a victim of this type of cybercrime.
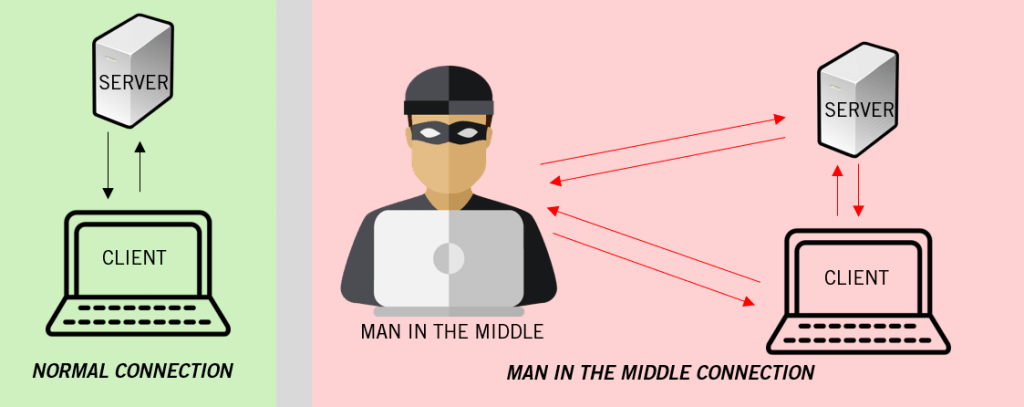
What is a Man-in-the-Middle Attack?
A Man-in-the-Middle (MITM) attack is a type of cyberattack where a malicious actor intercepts and potentially alters the communication between two parties without their knowledge. In essence, the attacker positions themselves between the sender and receiver, eavesdropping on or manipulating the data being exchanged. The victims believe they are communicating directly with each other, unaware that a third party is actively involved. This makes the MITM attack particularly dangerous as it exploits trust and can be difficult to detect.
How MITM Attacks Work
MITM attacks typically involve several stages:
- Interception: The attacker intercepts the communication stream between the two parties. This can be achieved through various methods, such as Wi-Fi eavesdropping, ARP spoofing, DNS spoofing, or SSL stripping.
- Decryption (if necessary): If the communication is encrypted, the attacker may attempt to decrypt the data. This could involve exploiting vulnerabilities in the encryption protocol or using brute-force techniques.
- Manipulation (optional): The attacker can modify the data being transmitted. This could involve altering financial transactions, stealing login credentials, or injecting malicious code.
- Re-encryption (if necessary): If the data was decrypted, the attacker re-encrypts it before forwarding it to the intended recipient. This helps maintain the illusion that the communication is secure.
- Forwarding: The attacker forwards the manipulated or unmanipulated data to the intended recipient. The recipient is unaware that the data has been intercepted.
Common Types of MITM Attacks
Wi-Fi Eavesdropping
This involves intercepting data transmitted over unsecured or poorly secured Wi-Fi networks. Attackers can set up fake Wi-Fi hotspots (evil twins) that mimic legitimate networks, enticing users to connect and unwittingly expose their data. Public Wi-Fi networks, often found in cafes or airports, are particularly vulnerable to MITM attacks.
ARP Spoofing
ARP (Address Resolution Protocol) spoofing involves sending falsified ARP messages over a local area network (LAN). By associating the attacker’s MAC address with the IP address of a legitimate device or server, the attacker can intercept traffic intended for that device. [See also: Network Security Best Practices]
DNS Spoofing
DNS (Domain Name System) spoofing, also known as DNS cache poisoning, involves injecting false DNS records into a DNS server’s cache. This can redirect users to malicious websites that mimic legitimate ones, allowing attackers to steal login credentials or install malware. A successful DNS spoofing MITM attack can affect a large number of users.
SSL Stripping
SSL (Secure Sockets Layer) stripping involves downgrading a secure HTTPS connection to an unencrypted HTTP connection. Attackers can use tools like SSLstrip to intercept the initial HTTPS request and redirect the user to an unencrypted version of the website. This allows them to intercept sensitive data transmitted over the insecure connection. Modern browsers are increasingly resistant to SSL stripping but it remains a potential threat.
HTTPS Spoofing
In HTTPS spoofing, attackers create a fake website that mimics a legitimate one, complete with a valid-looking SSL certificate. Unsuspecting users may enter sensitive information, believing they are on the real site. This type of man in the middle attack relies on user error and the difficulty in distinguishing genuine from fake websites.
Potential Consequences of MITM Attacks
The consequences of a successful MITM attack can be severe, both for individuals and organizations:
- Data Theft: Attackers can steal sensitive data such as login credentials, financial information, and personal data.
- Financial Loss: Attackers can manipulate financial transactions, diverting funds to their own accounts.
- Identity Theft: Stolen personal data can be used to commit identity theft.
- Malware Infection: Attackers can inject malicious code into the communication stream, infecting devices with malware.
- Reputational Damage: A successful MITM attack can damage an organization’s reputation and erode customer trust.
- Espionage: In some cases, MITM attacks are used for espionage, allowing attackers to intercept and monitor sensitive communications.
Preventing and Mitigating MITM Attacks
There are several steps that individuals and organizations can take to prevent and mitigate MITM attacks:
Use Strong Encryption
Ensure that all sensitive communications are encrypted using strong encryption protocols such as TLS (Transport Layer Security). This makes it more difficult for attackers to intercept and decrypt the data. Always look for the padlock icon in the browser address bar, indicating a secure HTTPS connection.
Use a VPN
A Virtual Private Network (VPN) encrypts all internet traffic, protecting it from eavesdropping. This is especially important when using public Wi-Fi networks. A VPN creates a secure tunnel between your device and a VPN server, preventing attackers from intercepting your data. Using a VPN can significantly reduce the risk of a successful man in the middle attack.
Be Wary of Public Wi-Fi
Avoid using unsecured public Wi-Fi networks for sensitive transactions. If you must use public Wi-Fi, use a VPN to encrypt your traffic. Be cautious of fake Wi-Fi hotspots that mimic legitimate networks. Verify the name of the Wi-Fi network with a trusted source before connecting.
Use Multi-Factor Authentication (MFA)
MFA adds an extra layer of security to your accounts, requiring a second factor of authentication in addition to your password. This makes it more difficult for attackers to gain access to your accounts, even if they have stolen your password. Enable MFA whenever possible, especially for sensitive accounts such as email, banking, and social media.
Keep Software Up-to-Date
Regularly update your operating system, web browser, and other software to patch security vulnerabilities. Software updates often include fixes for security flaws that could be exploited by attackers. Enable automatic updates to ensure that your software is always up-to-date.
Educate Users
Educate users about the risks of MITM attacks and how to recognize them. This includes teaching them to be wary of suspicious emails, websites, and Wi-Fi networks. Conduct regular security awareness training to keep users informed about the latest threats. A well-informed user is less likely to fall victim to a man in the middle attack.
Implement Network Security Measures
Organizations should implement network security measures such as firewalls, intrusion detection systems, and network segmentation to protect their networks from MITM attacks. These measures can help detect and prevent attackers from intercepting traffic and accessing sensitive data. [See also: Firewall Configuration Guide]
Monitor Network Traffic
Regularly monitor network traffic for suspicious activity. This can help detect MITM attacks in progress and allow you to take immediate action to mitigate the damage. Use network monitoring tools to analyze traffic patterns and identify anomalies.
Use DNSSEC
DNSSEC (Domain Name System Security Extensions) adds a layer of security to the DNS system, preventing DNS spoofing attacks. DNSSEC uses digital signatures to verify the authenticity of DNS records, ensuring that users are directed to the correct websites. Implementing DNSSEC can significantly reduce the risk of DNS spoofing MITM attacks.
Regular Security Audits
Conduct regular security audits to identify vulnerabilities in your systems and networks. This can help you identify and address potential weaknesses before they are exploited by attackers. Use penetration testing to simulate real-world attacks and assess the effectiveness of your security controls.
Conclusion
Man-in-the-Middle (MITM) attacks pose a significant threat to individuals and organizations. By understanding how these attacks work and implementing effective prevention and mitigation strategies, you can significantly reduce your risk. Staying vigilant, using strong security measures, and educating users are essential for protecting sensitive data and maintaining secure communications. Remember to always prioritize security and stay informed about the latest threats. By taking proactive steps, you can safeguard yourself and your organization from the potentially devastating consequences of a MITM attack.
