ICS Security: Protecting Critical Infrastructure in the Modern Age
In today’s interconnected world, the security of Industrial Control Systems (ICS) is paramount. These systems, which manage and control critical infrastructure like power grids, water treatment plants, and manufacturing facilities, are increasingly vulnerable to cyberattacks. A successful attack on an ICS can have devastating consequences, ranging from widespread power outages to contaminated water supplies and significant economic disruption. Understanding the complexities of ICS security and implementing robust protective measures is no longer optional; it’s a necessity.
Understanding Industrial Control Systems (ICS)
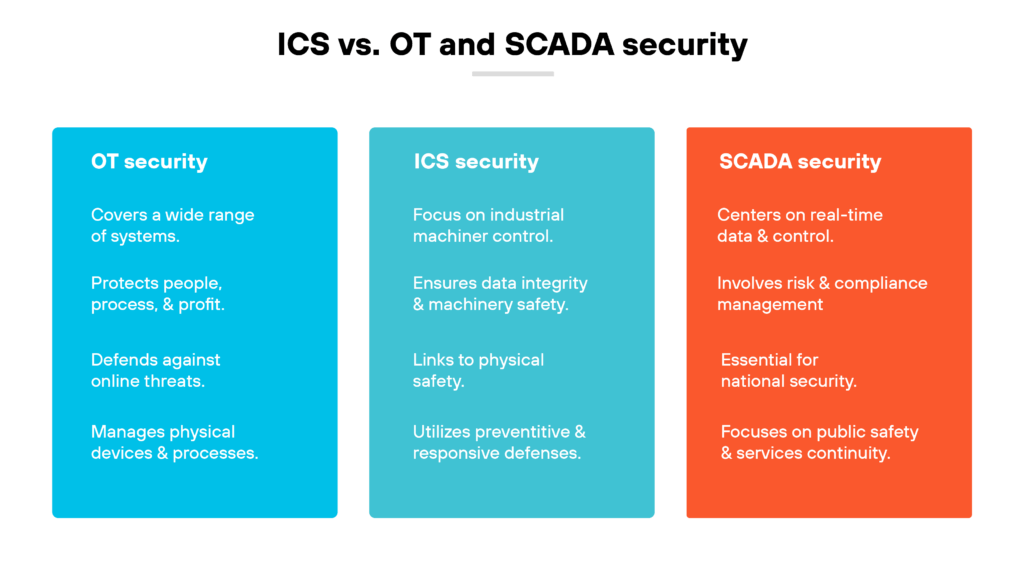
Industrial Control Systems (ICS) are a collection of hardware and software used to automate and control industrial processes. Unlike traditional IT systems, ICS are designed to interact directly with physical equipment, such as pumps, valves, and motors. Common types of ICS include:
- Supervisory Control and Data Acquisition (SCADA) systems: Used to monitor and control geographically dispersed assets, often across large areas. Think of pipeline management or electrical grid oversight.
- Distributed Control Systems (DCS): Employed in process-oriented industries like oil and gas, chemical manufacturing, and power generation to control complex processes within a localized area.
- Programmable Logic Controllers (PLCs): Small, specialized computers used to automate specific tasks, such as controlling machinery on a factory floor.
The convergence of IT and OT (Operational Technology) has blurred the lines between these systems, creating new attack vectors that malicious actors can exploit. Legacy ICS often lack the security features found in modern IT systems, making them particularly vulnerable. Addressing ICS security requires a holistic approach that considers both the technical and operational aspects of these systems.
The Growing Threat Landscape for ICS
The threat landscape for ICS security is constantly evolving. Nation-state actors, cybercriminals, and hacktivists are all increasingly targeting ICS for various reasons, including espionage, sabotage, and financial gain. Some notable examples of ICS attacks include:
- Stuxnet: A sophisticated worm that targeted Iranian nuclear facilities, demonstrating the potential for targeted attacks to cause physical damage.
- Industroyer/CrashOverride: A malware that caused a power outage in Ukraine, highlighting the vulnerability of power grids to cyberattacks.
- Triton/Trisis: A malware designed to target safety instrumented systems (SIS) in industrial facilities, potentially leading to catastrophic consequences.
These attacks demonstrate the sophistication and potential impact of ICS security breaches. The increasing connectivity of ICS to the internet and corporate networks has expanded the attack surface, making it easier for attackers to gain access to these systems. Furthermore, the lack of security awareness and training among ICS personnel can contribute to vulnerabilities.
Key Challenges in ICS Security
Securing ICS presents unique challenges that differ from traditional IT security. Some of the key challenges include:
- Legacy Systems: Many ICS are based on outdated technologies that were not designed with security in mind. Upgrading or replacing these systems can be costly and disruptive.
- Operational Constraints: ICS are often critical to operations, and any downtime can have significant consequences. Security measures must be implemented without disrupting operations.
- Lack of Visibility: Many organizations lack visibility into their ICS environments, making it difficult to detect and respond to security threats.
- Skills Gap: There is a shortage of skilled professionals with expertise in both IT and OT security.
- Complexity: ICS environments are often complex and heterogeneous, making it difficult to implement consistent security policies and procedures.
Overcoming these challenges requires a comprehensive and layered approach to ICS security, including implementing robust security controls, improving visibility, and investing in training and awareness programs.
Best Practices for ICS Security
Implementing a strong ICS security posture requires a multi-faceted approach. Here are some best practices to consider:
Asset Identification and Inventory
The first step in securing your ICS environment is to identify and inventory all assets, including hardware, software, and network devices. This will provide a baseline for understanding your security posture and identifying potential vulnerabilities. Use network scanning tools and manual inspections to create a complete inventory of your ICS assets.
Network Segmentation
Segment your ICS network from the corporate network to limit the impact of a potential breach. Implement firewalls and intrusion detection systems (IDS) to monitor and control network traffic between the ICS and corporate networks. [See also: Network Segmentation Strategies for Critical Infrastructure]
Access Control
Implement strong access control policies to restrict access to ICS components based on the principle of least privilege. Use multi-factor authentication (MFA) to protect against unauthorized access. Regularly review and update access control lists to ensure that only authorized personnel have access to sensitive systems.
Patch Management
Regularly patch ICS software and firmware to address known vulnerabilities. However, patching ICS can be challenging due to operational constraints. Develop a patch management process that includes testing patches in a non-production environment before deploying them to production systems. Consider using virtual patching solutions to mitigate vulnerabilities without disrupting operations.
Intrusion Detection and Prevention
Deploy intrusion detection and prevention systems (IDPS) to monitor network traffic and system logs for suspicious activity. Configure the IDPS to generate alerts when potential security incidents are detected. Integrate the IDPS with a security information and event management (SIEM) system to correlate events and provide a comprehensive view of your security posture.
Security Awareness Training
Provide regular security awareness training to ICS personnel to educate them about the latest threats and best practices for ICS security. Training should cover topics such as phishing, social engineering, and password security. Emphasize the importance of reporting suspicious activity to security personnel.
Incident Response Planning
Develop an incident response plan that outlines the steps to be taken in the event of a security breach. The plan should include procedures for identifying, containing, and recovering from incidents. Regularly test the incident response plan through tabletop exercises and simulations. [See also: Developing a Robust Incident Response Plan]
Regular Security Assessments
Conduct regular security assessments to identify vulnerabilities and weaknesses in your ICS security posture. These assessments should include penetration testing, vulnerability scanning, and security audits. Use the results of the assessments to prioritize remediation efforts and improve your overall security posture.
Physical Security
Don’t overlook the importance of physical security. Secure access to ICS equipment and facilities to prevent unauthorized access. Implement surveillance cameras, access control systems, and other physical security measures to protect against physical threats.
The Future of ICS Security
The future of ICS security will be shaped by several key trends, including the increasing adoption of cloud technologies, the proliferation of IoT devices, and the growing sophistication of cyberattacks. Organizations must adapt to these trends by investing in new security technologies, improving their security processes, and fostering a culture of security awareness. The integration of artificial intelligence (AI) and machine learning (ML) will play an increasingly important role in detecting and responding to ICS security threats. [See also: The Role of AI in Cybersecurity] Furthermore, collaboration between industry stakeholders, government agencies, and security vendors will be essential to address the evolving threat landscape.
Conclusion
ICS security is a critical concern for organizations that rely on industrial control systems to manage their operations. The potential consequences of a successful ICS attack can be devastating, ranging from widespread disruptions to significant economic losses and even physical harm. By understanding the threats, implementing best practices, and staying informed about the latest trends, organizations can significantly improve their ICS security posture and protect their critical infrastructure. Prioritizing ICS security is not just a matter of protecting assets; it’s a matter of protecting public safety and national security. Continuous monitoring, robust security protocols, and a proactive approach are crucial for maintaining a secure and resilient ICS security environment. Securing ICS security requires constant vigilance and adaptation to new threats as they emerge. Investing in ICS security is an investment in the future, ensuring the reliable and safe operation of critical infrastructure for years to come. Without proper attention to ICS security, organizations are leaving themselves vulnerable to potentially catastrophic attacks. Proper ICS security is vital for safeguarding our infrastructure. ICS security is a continuous process. ICS security needs to be prioritized. The importance of ICS security cannot be overstated. Effective ICS security is essential for protecting critical infrastructure. Strong ICS security is crucial for maintaining a safe and reliable environment. Implementing robust ICS security measures is a necessity in today’s threat landscape.
