IAM Platforms: Securing Access in the Modern Enterprise
In today’s complex digital landscape, Identity and Access Management (IAM) platforms are no longer optional; they are a critical component of any robust cybersecurity strategy. As organizations increasingly rely on cloud services, remote workforces, and a diverse array of applications, the need to control and monitor who has access to what – and when – has become paramount. This article delves into the world of IAM platforms, exploring their core functionalities, benefits, challenges, and future trends. We’ll examine how these platforms help organizations manage digital identities and enforce access policies, ultimately mitigating the risk of data breaches and ensuring regulatory compliance. The importance of IAM platforms cannot be overstated; they form the backbone of a secure and efficient IT environment. Effective IAM platforms provide granular control over access rights, ensuring that only authorized users can access sensitive resources. This is crucial for protecting valuable data and maintaining operational integrity. Companies are increasingly adopting sophisticated IAM platforms to streamline their security operations and improve their overall security posture.
Understanding Identity and Access Management (IAM)
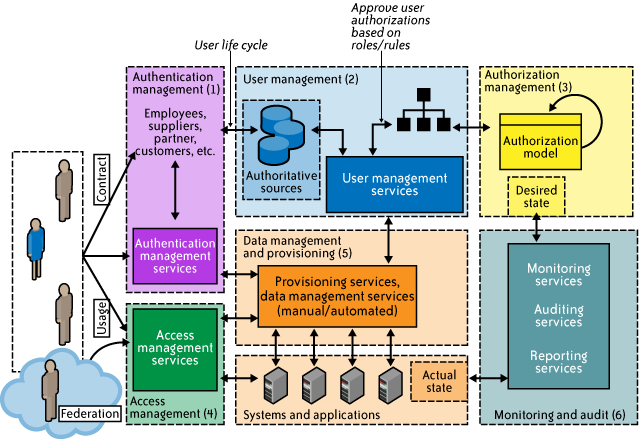
IAM is a framework of policies and technologies that ensures the right individuals have the appropriate access to technology resources. At its core, IAM is about managing digital identities – the unique representation of a user, device, or application within a system. These identities are then associated with specific privileges, defining what resources they can access and what actions they can perform. IAM platforms automate and streamline these processes, providing a centralized system for managing identities and access rights.
Key Components of an IAM Platform
- Identity Management: This includes creating, managing, and deleting user identities. It also involves managing user attributes, such as roles, departments, and job titles.
- Access Management: This focuses on controlling who has access to what resources. It involves defining access policies, enforcing authentication mechanisms, and authorizing access requests.
- Authentication: Verifying the identity of a user or device. Common authentication methods include passwords, multi-factor authentication (MFA), and biometrics.
- Authorization: Determining what resources a user or device is allowed to access after authentication. This is based on predefined access policies and user roles.
- Auditing and Reporting: Tracking user activity and generating reports for compliance and security purposes. This helps organizations identify potential security threats and ensure adherence to regulatory requirements.
Benefits of Implementing IAM Platforms
The benefits of implementing a robust IAM platform are numerous and far-reaching. They extend beyond just security, impacting operational efficiency, compliance, and the overall user experience.
Enhanced Security
The primary benefit of IAM platforms is enhanced security. By centralizing access control, organizations can significantly reduce the risk of unauthorized access and data breaches. Granular access policies ensure that users only have access to the resources they need, minimizing the potential for insider threats and accidental data leaks. Furthermore, IAM platforms often include features like adaptive authentication, which adjusts security measures based on user behavior and risk factors.
Improved Compliance
Many industries are subject to strict regulatory requirements regarding data privacy and security. IAM platforms help organizations comply with these regulations by providing a centralized system for managing access controls and generating audit trails. This simplifies the compliance process and reduces the risk of fines and penalties. Regulations like GDPR, HIPAA, and PCI DSS all require organizations to implement robust access controls, making IAM platforms an essential tool for compliance.
Increased Operational Efficiency
IAM platforms automate many of the manual tasks associated with identity and access management, freeing up IT staff to focus on more strategic initiatives. This includes automating user provisioning and deprovisioning, simplifying password management, and streamlining access request workflows. The result is a more efficient and productive IT environment. By automating routine tasks, IAM platforms reduce the administrative burden on IT teams and improve the speed and accuracy of access management processes.
Enhanced User Experience
While security is paramount, IAM platforms can also improve the user experience. Single sign-on (SSO) functionality allows users to access multiple applications with a single set of credentials, eliminating the need to remember multiple usernames and passwords. This simplifies the login process and reduces password fatigue. Furthermore, self-service portals allow users to manage their own profiles and request access to resources, empowering them and reducing the burden on IT support. A well-designed IAM platform can significantly improve user satisfaction and productivity.
Challenges of Implementing IAM Platforms
While the benefits of IAM platforms are clear, implementing them can be challenging. Organizations need to carefully plan and execute their IAM strategy to ensure a successful deployment.
Complexity
IAM platforms can be complex to implement and manage, especially in large and distributed organizations. Integrating with existing systems and applications can be challenging, and organizations need to carefully configure the platform to meet their specific needs. Furthermore, managing user roles and permissions can be a complex and time-consuming task. Organizations need to invest in training and expertise to effectively manage their IAM platform.
Cost
Implementing an IAM platform can be expensive, especially for smaller organizations. The costs include the software license, implementation services, and ongoing maintenance and support. Organizations need to carefully evaluate the costs and benefits of different IAM platforms to determine the best solution for their budget. However, it’s important to consider the long-term cost savings associated with improved security and operational efficiency.
User Adoption
Getting users to adopt a new IAM platform can be challenging. Users may resist changes to their login processes or be reluctant to use self-service portals. Organizations need to communicate the benefits of the new platform and provide adequate training to ensure user adoption. Furthermore, it’s important to design the platform with the user experience in mind, making it easy and intuitive to use.
Future Trends in IAM Platforms
The world of IAM is constantly evolving, driven by new technologies and changing business needs. Several key trends are shaping the future of IAM platforms.
Cloud-Based IAM
More and more organizations are moving their IAM infrastructure to the cloud. Cloud-based IAM platforms offer several advantages, including scalability, flexibility, and reduced costs. They also simplify integration with other cloud services and applications. As organizations increasingly rely on cloud-based resources, cloud-based IAM platforms will become increasingly important.
AI-Powered IAM
Artificial intelligence (AI) is being used to enhance IAM platforms in several ways. AI can be used to detect anomalous user behavior, automate access provisioning, and improve risk assessment. AI-powered IAM platforms can help organizations proactively identify and respond to security threats. For example, AI can analyze user login patterns to detect suspicious activity and automatically trigger additional authentication measures.
Passwordless Authentication
Passwordless authentication is gaining traction as a more secure and user-friendly alternative to traditional passwords. Passwordless authentication methods include biometrics, security keys, and one-time passcodes. IAM platforms are increasingly supporting passwordless authentication options, reducing the reliance on passwords and improving the user experience. This trend is driven by the increasing prevalence of phishing attacks and the growing recognition of the security risks associated with passwords.
Decentralized Identity
Decentralized identity, also known as self-sovereign identity (SSI), is a new approach to identity management that gives individuals control over their own digital identities. With decentralized identity, users can store their identity credentials on their own devices and share them selectively with relying parties. IAM platforms are beginning to support decentralized identity standards, enabling users to manage their own identities and control their personal data. This trend is driven by the growing concerns about data privacy and the desire for greater user control over personal information. [See also: Zero Trust Architecture]
Choosing the Right IAM Platform
Selecting the right IAM platform is a critical decision that can have a significant impact on an organization’s security posture and operational efficiency. Organizations should carefully evaluate their needs and requirements before choosing a platform. Here are some key factors to consider:
- Scalability: Can the platform scale to meet the organization’s growing needs?
- Integration: Does the platform integrate with existing systems and applications?
- Security: Does the platform offer robust security features, such as multi-factor authentication and adaptive authentication?
- Compliance: Does the platform help the organization comply with relevant regulations?
- User Experience: Is the platform easy to use for both administrators and end-users?
- Cost: Is the platform affordable and within the organization’s budget?
Conclusion
IAM platforms are an essential component of any modern cybersecurity strategy. They provide a centralized system for managing digital identities and enforcing access policies, helping organizations protect their valuable data and comply with regulatory requirements. While implementing an IAM platform can be challenging, the benefits are numerous, including enhanced security, improved compliance, increased operational efficiency, and enhanced user experience. As the threat landscape continues to evolve, IAM platforms will become increasingly important for organizations of all sizes. By carefully evaluating their needs and requirements, organizations can choose the right IAM platform to meet their specific needs and ensure a secure and efficient IT environment. The future of IAM platforms is bright, with new technologies like AI and decentralized identity promising to further enhance their capabilities and improve the user experience. [See also: Cloud Security Best Practices]
