IAM PAM Solutions: Securing Access and Managing Privileges in the Modern Enterprise
In today’s complex digital landscape, organizations face an ever-increasing array of cybersecurity threats. Protecting sensitive data and critical infrastructure requires a multi-layered approach, and two crucial components of any robust security strategy are Identity and Access Management (IAM) and Privileged Access Management (PAM). While often discussed separately, the integration of IAM PAM solutions provides a comprehensive framework for managing user identities, controlling access to resources, and safeguarding privileged accounts.
This article delves into the world of IAM PAM solutions, exploring their individual functionalities, the benefits of their integration, and the key considerations for implementation. We’ll examine the challenges that organizations face without effective IAM and PAM, and how these solutions mitigate risks, improve compliance, and enhance overall security posture.
Understanding Identity and Access Management (IAM)
IAM is the foundation of secure access control. It encompasses the policies, processes, and technologies used to manage digital identities and their access rights within an organization. The core functions of IAM include:
- User Provisioning and Deprovisioning: Creating, modifying, and deleting user accounts and assigning appropriate roles and permissions.
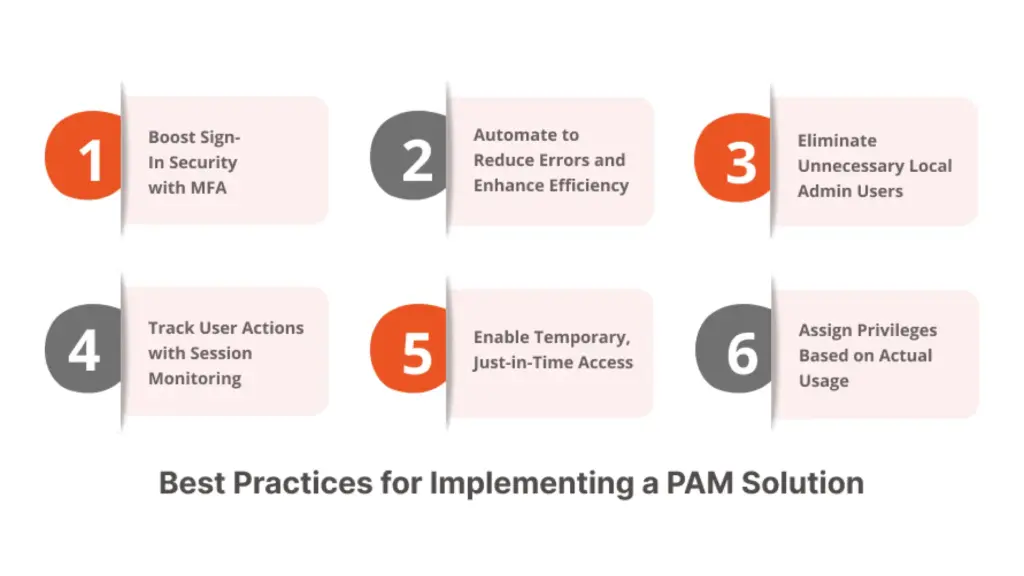
- Authentication: Verifying the identity of users attempting to access systems and applications. This can involve passwords, multi-factor authentication (MFA), and biometrics.
- Authorization: Determining what resources a user is allowed to access based on their role and permissions.
- Access Governance: Regularly reviewing and certifying user access rights to ensure they remain appropriate.
- Single Sign-On (SSO): Enabling users to access multiple applications with a single set of credentials.
A well-implemented IAM system streamlines user management, improves security, and enhances the user experience. By centralizing identity information and enforcing consistent access controls, IAM helps organizations prevent unauthorized access and data breaches. [See also: Implementing a Robust IAM Strategy]
Exploring Privileged Access Management (PAM)
PAM focuses specifically on managing and securing privileged accounts, which have elevated access rights to critical systems and data. These accounts are prime targets for attackers, as they can provide access to sensitive information and the ability to disrupt operations. Key features of PAM solutions include:
- Privileged Account Discovery: Identifying and inventorying all privileged accounts across the organization’s IT environment.
- Vaulting and Credential Management: Securely storing and managing privileged credentials, preventing them from being exposed or misused.
- Session Monitoring and Recording: Monitoring and recording privileged user sessions to detect suspicious activity and provide an audit trail.
- Just-in-Time (JIT) Access: Granting privileged access only when needed and for a limited duration, minimizing the risk of standing privileges.
- Privilege Elevation and Delegation: Allowing users to temporarily elevate their privileges to perform specific tasks, without granting them permanent administrative rights.
PAM solutions provide a critical layer of security by controlling and monitoring access to sensitive systems and data. By limiting the attack surface and detecting malicious activity, PAM helps organizations prevent data breaches, insider threats, and compliance violations. [See also: Best Practices for Privileged Access Management]
The Power of Integrated IAM PAM Solutions
While IAM and PAM address different aspects of access control, they are most effective when integrated. The synergy between IAM PAM solutions creates a comprehensive approach to security that addresses both user identities and privileged access. Benefits of integration include:
- Enhanced Security Posture: A unified approach to access management reduces the risk of security gaps and vulnerabilities.
- Improved Compliance: Integrated IAM PAM solutions help organizations meet regulatory requirements for data protection and access control.
- Streamlined Operations: Centralized management of identities and privileges simplifies administration and reduces operational overhead.
- Reduced Costs: Consolidating security tools and processes can lower overall costs and improve efficiency.
- Better Visibility and Control: A comprehensive view of user access and privileged activity provides better insights into potential risks.
For instance, integrating IAM with PAM can enable automated provisioning of privileged access based on user roles defined in the IAM system. This ensures that users only have the necessary privileges to perform their job functions, reducing the risk of unauthorized access. Furthermore, session monitoring and recording capabilities in PAM can be integrated with IAM’s audit logs to provide a complete audit trail of user activity, including both standard and privileged access. The combination of IAM PAM solutions offers a holistic security framework.
Key Considerations for Implementing IAM PAM Solutions
Implementing IAM PAM solutions requires careful planning and execution. Organizations should consider the following factors:
- Define Clear Goals and Objectives: Identify the specific security challenges that the solutions need to address and define measurable goals for success.
- Assess Current Infrastructure: Evaluate the existing IT environment, including applications, systems, and user populations.
- Choose the Right Solutions: Select IAM PAM solutions that meet the organization’s specific needs and integrate seamlessly with existing infrastructure. Consider factors such as scalability, ease of use, and vendor support.
- Develop a Comprehensive Implementation Plan: Outline the steps for deploying and configuring the solutions, including timelines, resource allocation, and training.
- Establish Strong Governance Policies: Define clear policies and procedures for managing identities, access rights, and privileged accounts.
- Provide User Training: Educate users about the new security protocols and how to use the IAM PAM solutions effectively.
- Monitor and Maintain the Solutions: Continuously monitor the performance of the solutions and make necessary adjustments to ensure they remain effective.
A phased approach to implementation is often recommended, starting with a pilot project to test the solutions and refine the implementation plan. Organizations should also involve key stakeholders from IT, security, and business units to ensure that the solutions meet their needs and requirements. The implementation of IAM PAM solutions is a continuous process requiring ongoing monitoring and adaptation.
Challenges and Mitigation Strategies
Implementing and managing IAM PAM solutions can present several challenges:
- Complexity: Integrating diverse systems and applications can be complex and require specialized expertise. Mitigation: Choose solutions that offer seamless integration and provide comprehensive documentation and support.
- User Resistance: Users may resist changes to their access privileges or authentication methods. Mitigation: Communicate the benefits of the solutions and provide adequate training and support.
- Scalability: The solutions must be able to scale to accommodate the organization’s growing needs. Mitigation: Choose solutions that are designed for scalability and can handle increasing user populations and data volumes.
- Cost: Implementing and maintaining IAM PAM solutions can be expensive. Mitigation: Conduct a thorough cost-benefit analysis and choose solutions that offer the best value for the organization’s budget.
- Lack of Awareness: Insufficient understanding of the importance of IAM and PAM can hinder implementation efforts. Mitigation: Conduct awareness campaigns and provide training to educate employees about the benefits of these solutions.
Addressing these challenges requires a proactive approach, strong leadership, and a commitment to ongoing improvement. Regularly reviewing and updating the IAM PAM solutions and related policies is crucial to maintaining a strong security posture. [See also: Overcoming Common IAM Challenges]
The Future of IAM PAM Solutions
The landscape of IAM PAM solutions is constantly evolving, driven by emerging technologies and changing security threats. Some key trends shaping the future of IAM and PAM include:
- Cloud-Based Solutions: Increasing adoption of cloud-based IAM and PAM solutions offers scalability, flexibility, and cost savings.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are being used to automate tasks, detect anomalies, and improve security intelligence.
- Biometric Authentication: Growing use of biometric authentication methods, such as fingerprint scanning and facial recognition, enhances security and improves user experience.
- Zero Trust Architecture: The principles of Zero Trust, which assume that no user or device should be trusted by default, are being integrated into IAM and PAM strategies.
- DevSecOps Integration: Integrating security into the DevOps pipeline ensures that security considerations are addressed throughout the software development lifecycle.
As organizations continue to embrace digital transformation, the importance of IAM PAM solutions will only increase. By staying informed about the latest trends and technologies, organizations can ensure that their access management strategies remain effective in protecting their sensitive data and critical infrastructure.
Conclusion
IAM PAM solutions are essential components of a comprehensive cybersecurity strategy. By managing user identities, controlling access to resources, and safeguarding privileged accounts, these solutions help organizations mitigate risks, improve compliance, and enhance their overall security posture. While implementation can be challenging, the benefits of integrated IAM PAM solutions far outweigh the costs. Organizations that invest in robust IAM PAM solutions are better positioned to protect themselves from the ever-evolving threat landscape and maintain a secure and resilient IT environment. The future of security relies heavily on the proper implementation and management of IAM PAM solutions. It’s an ongoing process that demands attention and resources to safeguard valuable digital assets.
