How Does an Intrusion Detection System (IDS) Work? A Comprehensive Guide
In today’s digital landscape, cybersecurity threats are constantly evolving, posing significant risks to organizations of all sizes. An Intrusion Detection System (IDS) is a crucial component of a robust security posture, acting as a vigilant sentinel monitoring network traffic and system activity for malicious behavior. This comprehensive guide delves into the inner workings of an IDS, exploring its functionalities, types, deployment strategies, and limitations.
Understanding how an IDS works is paramount for IT professionals and anyone concerned with protecting sensitive data and maintaining operational integrity. This article aims to provide a clear and concise explanation of the core principles behind intrusion detection systems, empowering you to make informed decisions about security investments and strategies.
What is an Intrusion Detection System (IDS)?
An Intrusion Detection System (IDS) is a security tool that monitors a network or system for malicious activity or policy violations. It analyzes network traffic, system logs, and other data sources to identify suspicious patterns and alert administrators to potential threats. Unlike Intrusion Prevention Systems (IPS), an IDS primarily focuses on detection, leaving the blocking or mitigation of threats to other security tools or manual intervention. [See also: IDS vs IPS: Key Differences and When to Use Each]
Key Components of an IDS
An IDS typically comprises several key components that work together to detect and respond to security threats:
- Sensors: These components are responsible for collecting data from various sources, such as network traffic, system logs, and host activity. Sensors can be deployed at different points within the network to provide comprehensive coverage.
- Analysis Engine: The analysis engine is the brain of the IDS, responsible for processing the data collected by the sensors and identifying suspicious patterns. It uses various detection techniques, such as signature-based detection, anomaly-based detection, and policy-based detection.
- Signature Database: This database contains a collection of known attack signatures, which are patterns of malicious activity that can be used to identify specific threats. The IDS compares the data collected by the sensors against these signatures to detect known attacks.
- Management Console: The management console provides a central interface for configuring, monitoring, and managing the IDS. It allows administrators to view alerts, generate reports, and adjust the system’s settings.
How Does an IDS Work? A Deep Dive
The operation of an IDS can be broken down into several key steps:
- Data Collection: Sensors collect data from various sources, such as network traffic, system logs, and host activity. This data is then transmitted to the analysis engine.
- Data Analysis: The analysis engine processes the collected data and compares it against known attack signatures and established baselines of normal activity. It uses various detection techniques to identify suspicious patterns.
- Alert Generation: When the IDS detects a suspicious pattern, it generates an alert. The alert typically includes information about the detected activity, such as the source and destination IP addresses, the type of attack, and the severity level.
- Alert Notification: The IDS notifies administrators of the alert through various channels, such as email, SMS, or a dedicated management console.
- Response: Administrators review the alert and take appropriate action, such as investigating the incident, blocking the malicious traffic, or isolating the affected system.
Types of Intrusion Detection Systems
IDS can be broadly classified into several types, based on their deployment location and detection methods:
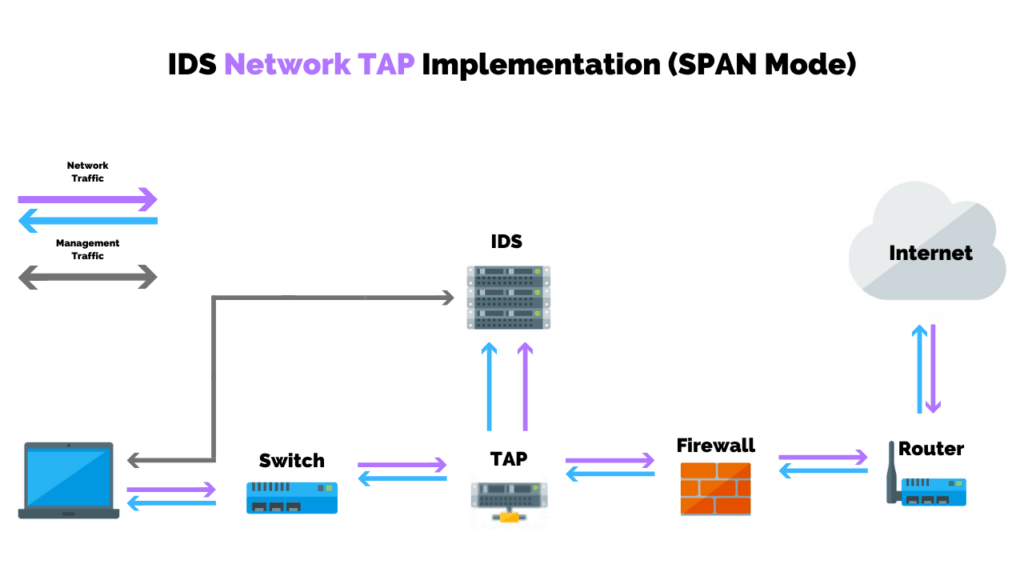
Network Intrusion Detection System (NIDS)
A NIDS monitors network traffic for suspicious activity. It is typically deployed at strategic points within the network, such as at the perimeter or on critical network segments. NIDS analyzes network packets to identify malicious patterns, such as denial-of-service attacks, port scans, and malware infections.
Host Intrusion Detection System (HIDS)
A HIDS monitors activity on a specific host system for suspicious behavior. It analyzes system logs, file integrity, and process activity to detect threats such as malware infections, unauthorized access, and privilege escalation attacks. HIDS is typically deployed on critical servers and workstations.
Signature-Based Detection
Signature-based detection relies on a database of known attack signatures to identify malicious activity. The IDS compares the data collected by the sensors against these signatures to detect known attacks. This method is effective at detecting well-known threats, but it is less effective at detecting new or unknown attacks.
Anomaly-Based Detection
Anomaly-based detection establishes a baseline of normal activity and then detects deviations from that baseline. The IDS learns what is considered normal behavior for the network or system and then flags any activity that falls outside of that range. This method is effective at detecting new or unknown attacks, but it can also generate false positives.
Policy-Based Detection
Policy-based detection relies on predefined security policies to identify violations. The IDS monitors network traffic and system activity to ensure that they comply with the established policies. This method is effective at enforcing security policies and preventing unauthorized activity.
Advantages of Using an IDS
Implementing an Intrusion Detection System offers several key benefits:
- Early Threat Detection: An IDS provides early warning of potential security threats, allowing organizations to respond quickly and prevent damage.
- Comprehensive Monitoring: An IDS monitors network traffic, system logs, and host activity, providing comprehensive visibility into the security posture of the organization.
- Compliance: Many regulations and standards require organizations to implement security controls, such as an IDS, to protect sensitive data.
- Improved Security Posture: An IDS helps organizations to improve their overall security posture by identifying and mitigating security vulnerabilities.
Limitations of an IDS
While IDS are valuable security tools, they also have some limitations:
- False Positives: IDS can generate false positives, which are alerts that indicate a threat when no actual threat exists. False positives can be time-consuming to investigate and can distract from real threats.
- False Negatives: IDS can also generate false negatives, which are failures to detect actual threats. False negatives can be caused by various factors, such as outdated signatures, misconfigured settings, or sophisticated attacks that evade detection.
- Performance Impact: IDS can have a performance impact on the network or system that it is monitoring. The impact can be minimized by carefully tuning the system’s settings and deploying it in a way that minimizes latency.
- Limited Response Capabilities: An IDS primarily focuses on detection, leaving the blocking or mitigation of threats to other security tools or manual intervention. [See also: Integrating IDS and IPS for Enhanced Security]
Best Practices for Deploying and Managing an IDS
To maximize the effectiveness of an Intrusion Detection System, it is important to follow best practices for deployment and management:
- Define Clear Security Policies: Establish clear security policies that define what is considered acceptable and unacceptable behavior on the network and systems.
- Choose the Right Type of IDS: Select the type of IDS that is best suited for your organization’s needs and environment.
- Properly Configure the IDS: Configure the IDS to accurately detect threats and minimize false positives.
- Regularly Update Signatures: Keep the IDS signature database up to date with the latest threat information.
- Monitor Alerts and Investigate Incidents: Monitor alerts generated by the IDS and investigate incidents promptly.
- Tune the IDS: Regularly tune the IDS settings to optimize performance and accuracy.
- Provide Training: Provide training to IT staff on how to use and manage the IDS.
Conclusion
An Intrusion Detection System is an essential security tool for organizations seeking to protect their networks and systems from malicious activity. By understanding how an IDS works, its different types, and its limitations, organizations can effectively deploy and manage an IDS to enhance their overall security posture. While not a silver bullet, an IDS, when properly implemented and maintained, provides a critical layer of defense against the ever-evolving threat landscape. Remember to regularly review and update your IDS configurations and security policies to stay ahead of emerging threats and ensure the ongoing protection of your valuable data and systems. This proactive approach is key to maintaining a resilient and secure environment in today’s digital world.
