Essential DAST Tools List: A Comprehensive Guide for Application Security
In today’s rapidly evolving digital landscape, ensuring the security of web applications is paramount. A critical component of a robust security strategy is Dynamic Application Security Testing (DAST). This methodology involves testing an application while it’s running, simulating real-world attacks to identify vulnerabilities. This comprehensive DAST tools list will explore some of the most effective tools available, helping you make informed decisions to protect your applications.
Understanding DAST: The Basics
Before diving into the DAST tools list, it’s important to understand what DAST is and why it’s crucial. DAST solutions analyze applications from the outside in, identifying vulnerabilities that could be exploited by malicious actors. Unlike Static Application Security Testing (SAST), which examines source code, DAST focuses on the application’s behavior during runtime. This makes it particularly effective at finding vulnerabilities that arise from configuration issues, server misconfigurations, and runtime errors.
The primary goal of DAST is to simulate attacks and identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and broken authentication. By mimicking the actions of a hacker, DAST tools can uncover weaknesses that might otherwise go unnoticed. Incorporating DAST into your software development lifecycle (SDLC) is crucial for proactive security management.
Key Features to Look for in DAST Tools
When evaluating a DAST tools list, several key features should be considered to ensure the tool meets your specific needs:
- Comprehensive Vulnerability Coverage: The tool should be able to detect a wide range of vulnerabilities, including OWASP Top 10 and other emerging threats.
- Ease of Use: A user-friendly interface and intuitive workflow are essential for efficient testing.
- Integration Capabilities: The tool should integrate seamlessly with your existing development and security tools, such as CI/CD pipelines and issue trackers.
- Customization Options: The ability to customize scans and reports is crucial for tailoring the tool to your specific application environment.
- Reporting and Analysis: The tool should provide detailed reports with actionable insights and remediation recommendations.
- Scalability: The tool should be able to handle large and complex applications without performance issues.
Top DAST Tools List: A Detailed Overview
Here’s a curated DAST tools list, featuring some of the leading solutions in the market:
1. Burp Suite Professional
Burp Suite Professional is a widely used DAST tool favored by security professionals. It offers a comprehensive suite of features for web application security testing, including a proxy, scanner, and intruder. Burp Suite is particularly strong in identifying vulnerabilities like SQL injection, XSS, and CSRF. Its extensibility through plugins makes it a versatile choice for various testing scenarios.
2. OWASP ZAP (Zed Attack Proxy)
OWASP ZAP is a free and open-source DAST tool maintained by the Open Web Application Security Project (OWASP). It’s designed to be easy to use, making it suitable for both beginners and experienced security testers. ZAP offers features like automated scanning, passive scanning, and a proxy for intercepting and modifying HTTP traffic. The tool’s active community and frequent updates ensure it remains a relevant and effective option. This inclusion in the DAST tools list is due to its accessibility and robust feature set.
3. Acunetix
Acunetix is a commercial DAST tool that provides automated vulnerability scanning and management. It’s known for its accuracy and speed, making it a popular choice for organizations looking to streamline their security testing process. Acunetix supports a wide range of web technologies and offers advanced features like incremental scanning and vulnerability prioritization. The detailed reporting and integration capabilities make it a valuable addition to any security toolkit.
4. Netsparker
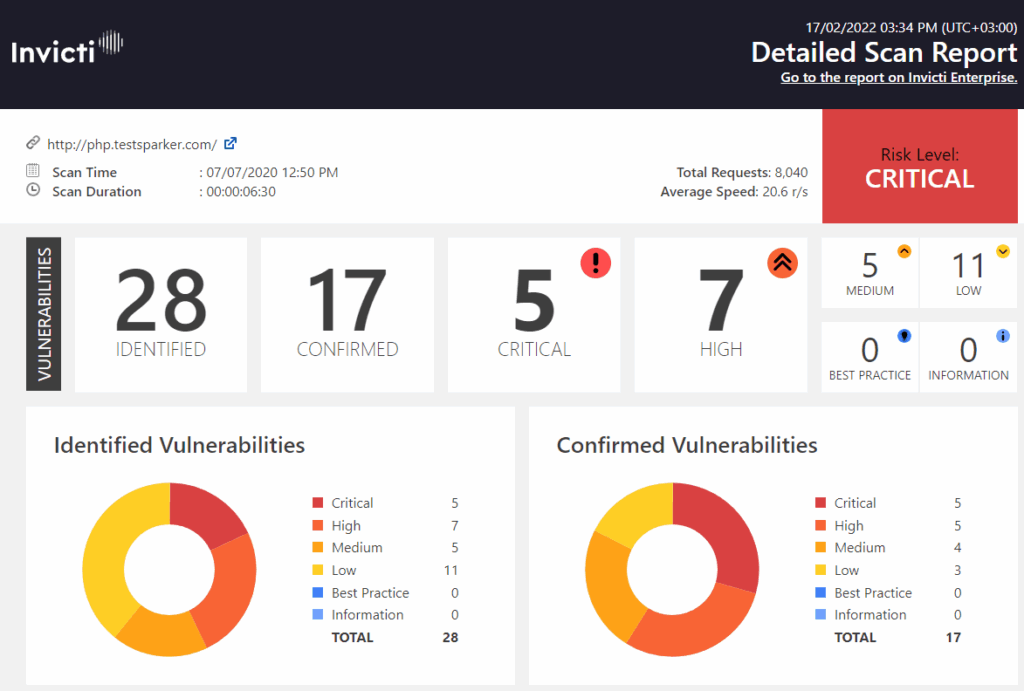
Netsparker, now known as Invicti, is another leading commercial DAST tool that focuses on automation and accuracy. It uses a unique Proof-Based Scanning technology to automatically verify vulnerabilities, reducing false positives. Netsparker supports both web and web API scanning and offers robust reporting and integration features. Its ability to automatically confirm vulnerabilities sets it apart from other tools in the DAST tools list.
5. Veracode Dynamic Analysis
Veracode Dynamic Analysis is a cloud-based DAST solution that integrates with Veracode’s broader application security platform. It offers automated scanning and vulnerability management, providing comprehensive visibility into application security risks. Veracode’s platform also includes SAST and SCA capabilities, making it a comprehensive solution for organizations looking to address security across the entire SDLC.
6. Rapid7 InsightAppSec
Rapid7 InsightAppSec is a DAST tool that focuses on providing actionable insights and rapid remediation. It offers automated scanning, vulnerability prioritization, and integration with Rapid7’s other security tools, such as InsightVM and InsightIDR. InsightAppSec is designed to help organizations quickly identify and address security risks in their web applications.
7. Qualys Web Application Scanning
Qualys Web Application Scanning is a cloud-based DAST solution that provides automated vulnerability scanning and compliance reporting. It’s part of the Qualys Cloud Platform, which offers a comprehensive suite of security and compliance tools. Qualys WAS is known for its accuracy and scalability, making it suitable for organizations of all sizes. Its integration with other Qualys modules provides a unified view of security risks.
8. StackHawk
StackHawk is a DAST tool designed for modern development workflows. It integrates directly into CI/CD pipelines, allowing developers to catch vulnerabilities early in the development process. StackHawk is particularly well-suited for organizations adopting a DevOps or DevSecOps approach. Its developer-friendly interface and automated scanning capabilities make it a valuable tool for improving application security. The inclusion in this DAST tools list highlights its modern approach to security.
9. HCL AppScan
HCL AppScan is a comprehensive DAST tool that offers automated scanning, manual testing, and reporting capabilities. It supports a wide range of web technologies and provides detailed vulnerability information and remediation recommendations. HCL AppScan is a mature and well-established DAST solution with a strong track record.
10. Detectify
Detectify is a DAST tool that uses crowdsourced security research to identify vulnerabilities. It offers automated scanning and continuous monitoring, providing real-time insights into application security risks. Detectify’s unique approach to vulnerability detection makes it a valuable addition to any security program. It is a modern tool in this DAST tools list.
Choosing the Right DAST Tool
Selecting the right DAST tool depends on your organization’s specific needs and requirements. Consider factors such as the size and complexity of your applications, your budget, and your existing security infrastructure. It’s often helpful to conduct a trial or proof-of-concept with several tools to determine which one best meets your needs. Remember to evaluate the tool’s accuracy, ease of use, integration capabilities, and reporting features.
When evaluating tools from this DAST tools list, consider the following questions:
- Does the tool support the technologies used in your applications?
- Does the tool integrate with your existing development and security tools?
- Does the tool provide detailed and actionable reports?
- Does the tool offer adequate support and documentation?
- Is the tool scalable to meet your future needs?
Integrating DAST into the SDLC
To maximize the effectiveness of DAST, it should be integrated into the software development lifecycle (SDLC). This involves incorporating DAST into your CI/CD pipelines and making it a regular part of your testing process. By identifying vulnerabilities early in the development process, you can reduce the cost and effort required to fix them. Integrating DAST also helps to ensure that security is considered throughout the entire development process, rather than being an afterthought.
Consider these steps when integrating DAST:
- Define clear security requirements: Establish clear security requirements for your applications and ensure that these requirements are communicated to the development team.
- Automate DAST scans: Automate DAST scans as part of your CI/CD pipeline to ensure that every build is tested for vulnerabilities.
- Prioritize vulnerabilities: Prioritize vulnerabilities based on their severity and impact, and focus on remediating the most critical issues first.
- Provide training and awareness: Provide training and awareness to developers on common vulnerabilities and how to avoid them.
- Continuously monitor your applications: Continuously monitor your applications for new vulnerabilities and security threats.
Best Practices for Using DAST Tools
To get the most out of your DAST tools, follow these best practices:
- Regularly update your tools: Keep your DAST tools up to date with the latest vulnerability definitions and security patches.
- Configure your scans properly: Configure your scans to accurately reflect your application environment and testing requirements.
- Validate scan results: Validate scan results to ensure that vulnerabilities are accurately identified and prioritized.
- Remediate vulnerabilities promptly: Remediate vulnerabilities promptly to reduce the risk of exploitation.
- Document your testing process: Document your testing process to ensure that it is consistent and repeatable.
The Future of DAST
The field of DAST is constantly evolving, with new tools and techniques emerging to address the latest security threats. As applications become more complex and the threat landscape becomes more sophisticated, DAST will continue to play a critical role in ensuring application security. Emerging trends in DAST include the use of artificial intelligence (AI) and machine learning (ML) to improve vulnerability detection and prioritization, as well as the integration of DAST with other security tools and platforms. This DAST tools list will undoubtedly expand and evolve as technology advances.
DAST tools are essential for identifying vulnerabilities in web applications. By incorporating DAST into your SDLC and following best practices, you can significantly improve your application security posture. This DAST tools list provides a starting point for evaluating different DAST solutions and choosing the one that best meets your needs. Remember to consider factors such as vulnerability coverage, ease of use, integration capabilities, and reporting features when making your decision. Regularly reviewing and updating your security practices, including your choice of DAST tools, is crucial for staying ahead of evolving threats. [See also: SAST vs DAST: Choosing the Right Security Testing Method] [See also: Application Security Best Practices] [See also: The Importance of Penetration Testing]
