Enterprise VPNs: Securing Your Business in a Connected World
In today’s interconnected world, businesses face an ever-growing number of cybersecurity threats. One crucial tool for mitigating these risks and ensuring secure access to sensitive data is the enterprise VPN. An enterprise VPN, or Virtual Private Network, provides a secure and encrypted connection for employees accessing the company network remotely, whether they’re working from home, traveling, or connecting from a public Wi-Fi hotspot. This article delves into the importance of enterprise VPNs, their functionalities, benefits, implementation considerations, and the future of this essential security technology.
Understanding Enterprise VPNs
Unlike personal VPNs that primarily focus on privacy and bypassing geo-restrictions, enterprise VPNs are designed to address the specific security and compliance needs of organizations. They go beyond simply masking IP addresses and encrypting traffic. Enterprise VPNs offer a centralized management system, allowing IT administrators to control access, enforce security policies, and monitor network activity. This is crucial for maintaining data integrity and preventing unauthorized access to confidential information.
How Enterprise VPNs Work
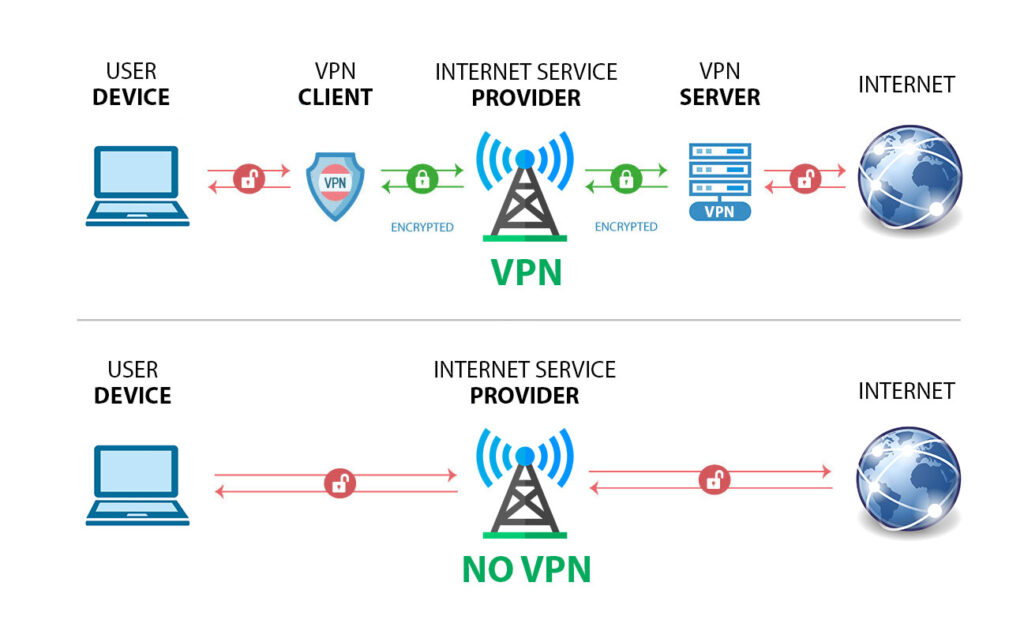
An enterprise VPN creates a secure tunnel between an employee’s device and the company network. When an employee connects to the enterprise VPN, their internet traffic is encrypted and routed through a VPN server. This server acts as an intermediary, masking the employee’s IP address and shielding their data from potential eavesdroppers. The encryption process ensures that even if the data is intercepted, it remains unreadable to unauthorized parties. Furthermore, the VPN authenticates the user, verifying their identity and ensuring they have the necessary permissions to access specific resources on the network.
Key Features of Enterprise VPNs
- Strong Encryption: Utilizes robust encryption protocols like AES-256 to protect data in transit.
- Authentication: Employs multi-factor authentication (MFA) to verify user identities.
- Access Control: Allows granular control over which resources users can access based on their roles and responsibilities.
- Centralized Management: Provides a centralized platform for managing VPN connections, policies, and users.
- Logging and Auditing: Tracks user activity and provides audit trails for compliance purposes.
- Split Tunneling: Enables users to access local network resources while still being connected to the enterprise VPN.
- Kill Switch: Automatically disconnects the user from the internet if the VPN connection drops, preventing unencrypted data from being exposed.
Benefits of Implementing an Enterprise VPN
Implementing an enterprise VPN offers numerous benefits for businesses of all sizes. These benefits extend beyond basic security and contribute to increased productivity, improved compliance, and enhanced business continuity.
Enhanced Security
The primary benefit of an enterprise VPN is enhanced security. By encrypting data and authenticating users, it protects sensitive information from unauthorized access, data breaches, and cyberattacks. This is particularly important for organizations that handle sensitive customer data, financial information, or intellectual property. An enterprise VPN helps prevent man-in-the-middle attacks, data interception on public Wi-Fi, and unauthorized access to internal resources.
Improved Compliance
Many industries are subject to strict regulatory requirements regarding data security and privacy. An enterprise VPN can help organizations comply with these regulations, such as HIPAA, GDPR, and PCI DSS. By providing a secure and auditable connection, it demonstrates a commitment to protecting sensitive data and meeting compliance obligations.
Increased Productivity
An enterprise VPN enables employees to work remotely without compromising security. This can lead to increased productivity and improved employee satisfaction. Employees can securely access company resources from anywhere in the world, allowing them to stay connected and productive even when they’re away from the office. The flexibility offered by an enterprise VPN can also improve employee morale and reduce absenteeism.
Enhanced Business Continuity
In the event of a disaster or unexpected event, an enterprise VPN can help ensure business continuity. Employees can continue to work remotely and access critical resources, even if the physical office is inaccessible. This can minimize disruption and help the organization recover quickly from any unforeseen circumstances. An enterprise VPN is a crucial component of a comprehensive business continuity plan.
Cost Savings
While there is an initial investment in implementing an enterprise VPN, it can lead to long-term cost savings. By enabling remote work, organizations can reduce their office space requirements and lower overhead costs. Furthermore, by preventing data breaches and cyberattacks, an enterprise VPN can help avoid costly fines, legal fees, and reputational damage.
Implementing an Enterprise VPN: Key Considerations
Implementing an enterprise VPN requires careful planning and consideration. It’s crucial to choose the right VPN solution, configure it properly, and train employees on how to use it effectively. Here are some key considerations for implementing an enterprise VPN:
Choosing the Right VPN Solution
There are many different enterprise VPN solutions available on the market, each with its own features and capabilities. It’s important to choose a solution that meets the specific needs of your organization. Consider factors such as the number of users, the level of security required, the budget, and the ease of management. Look for a solution that offers strong encryption, multi-factor authentication, centralized management, and comprehensive logging and auditing capabilities. Research different vendors and read reviews to make an informed decision.
Configuring the VPN
Proper configuration is essential for ensuring the security and effectiveness of the enterprise VPN. Configure the VPN to use strong encryption protocols, enforce multi-factor authentication, and implement strict access control policies. Regularly review and update the configuration to address any vulnerabilities or changes in the threat landscape. Ensure that the VPN is integrated with other security systems, such as firewalls and intrusion detection systems, to provide a comprehensive security posture.
Training Employees
Employees need to be trained on how to use the enterprise VPN properly and securely. They should understand the importance of connecting to the VPN when accessing company resources remotely and how to recognize and avoid phishing attacks. Provide clear and concise instructions on how to connect to the VPN, troubleshoot common issues, and report any security concerns. Regularly reinforce security awareness training to keep employees informed about the latest threats and best practices. The success of an enterprise VPN relies heavily on employee compliance and understanding.
Monitoring and Maintenance
Once the enterprise VPN is implemented, it’s important to monitor its performance and maintain it regularly. Monitor VPN connections, user activity, and security logs to identify any potential issues or anomalies. Regularly update the VPN software to address any vulnerabilities and ensure compatibility with the latest operating systems and devices. Perform regular security audits to assess the effectiveness of the VPN and identify areas for improvement. Proactive monitoring and maintenance are crucial for maintaining the security and reliability of the enterprise VPN.
The Future of Enterprise VPNs
The future of enterprise VPNs is evolving rapidly, driven by advancements in technology and the changing needs of businesses. As organizations increasingly adopt cloud-based services and embrace remote work, the role of enterprise VPNs will become even more critical. Here are some key trends shaping the future of enterprise VPNs:
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) is an emerging security model that takes a more granular approach to access control. Instead of granting access based on network location, ZTNA verifies the identity and context of each user and device before granting access to specific resources. ZTNA is often seen as a replacement for traditional enterprise VPNs, offering a more secure and flexible approach to remote access.
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP) is another emerging security model that focuses on creating a secure perimeter around applications and data, rather than the entire network. SDP uses identity-based access control and micro-segmentation to restrict access to only authorized users and devices. SDP can be used in conjunction with enterprise VPNs to provide an additional layer of security for sensitive applications and data.
Integration with Cloud Security Platforms
As organizations increasingly migrate to the cloud, enterprise VPNs are becoming more integrated with cloud security platforms. This integration allows organizations to extend their security policies and controls to the cloud, ensuring consistent security across all environments. Cloud security platforms offer features such as threat detection, data loss prevention, and compliance monitoring, which can enhance the security of enterprise VPNs.
AI and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are being used to enhance the security and performance of enterprise VPNs. AI and ML can be used to detect and prevent threats, optimize VPN performance, and automate security tasks. For example, AI can be used to identify anomalous user behavior or detect malware infections, while ML can be used to predict network congestion and optimize VPN routing. These technologies will continue to play an increasingly important role in the future of enterprise VPNs.
Conclusion
Enterprise VPNs are an essential security tool for businesses of all sizes. They provide a secure and encrypted connection for employees accessing the company network remotely, protecting sensitive data from unauthorized access and cyberattacks. By implementing an enterprise VPN, organizations can enhance security, improve compliance, increase productivity, and ensure business continuity. While emerging technologies like ZTNA and SDP are gaining traction, enterprise VPNs will continue to play a vital role in securing remote access for years to come. Choosing the right VPN solution, configuring it properly, and training employees on how to use it effectively are crucial for maximizing the benefits of an enterprise VPN. As the threat landscape continues to evolve, organizations must stay informed about the latest security technologies and adapt their security strategies accordingly. [See also: Remote Access Security Best Practices] [See also: Choosing the Right VPN Protocol] [See also: The Importance of Data Encryption]
