Choosing the Right Vulnerability Management Solutions: A Comprehensive Guide
In today’s complex digital landscape, where cyber threats are constantly evolving, effective vulnerability management solutions are no longer optional – they are essential. Organizations of all sizes face a barrage of potential weaknesses in their systems, applications, and networks. These vulnerabilities, if left unaddressed, can be exploited by malicious actors, leading to data breaches, financial losses, reputational damage, and legal repercussions. Therefore, understanding and implementing robust vulnerability management solutions is critical for maintaining a strong security posture.
This comprehensive guide will explore the key aspects of vulnerability management solutions, helping you understand what they are, why they’re important, and how to choose the right solution for your organization’s specific needs. We’ll delve into the different types of solutions available, the factors to consider when making your decision, and best practices for implementing and maintaining an effective vulnerability management program. By the end of this article, you’ll have a clear understanding of how to leverage vulnerability management solutions to protect your organization from cyber threats.
Understanding Vulnerability Management
Before diving into specific vulnerability management solutions, it’s crucial to understand the underlying concept of vulnerability management itself. Vulnerability management is a cyclical process encompassing the identification, assessment, remediation, and reporting of security vulnerabilities within an organization’s IT infrastructure. It’s a proactive approach to security that aims to identify and address weaknesses before they can be exploited.
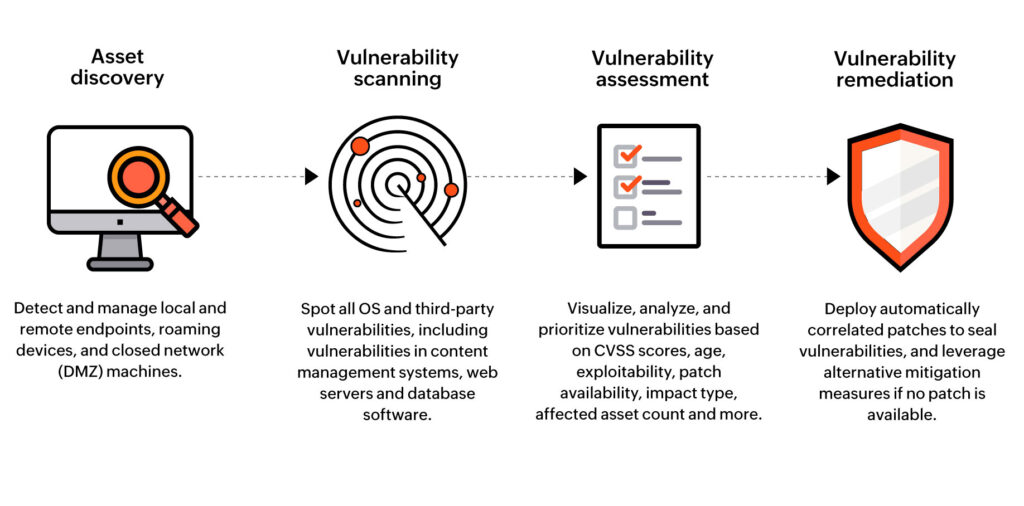
The Vulnerability Management Lifecycle
The vulnerability management lifecycle typically consists of the following phases:
- Identification: This involves scanning systems, applications, and networks to identify potential vulnerabilities. This can be done using automated scanning tools or manual assessments.
- Assessment: Once vulnerabilities are identified, they need to be assessed to determine their severity and potential impact. This involves analyzing the vulnerability’s characteristics, the affected assets, and the likelihood of exploitation.
- Remediation: This involves taking steps to address the identified vulnerabilities. This can include patching software, configuring systems securely, or implementing compensating controls.
- Reporting: This involves documenting the vulnerability management process, including the identified vulnerabilities, the assessment results, and the remediation actions taken. This information is used to track progress, identify trends, and improve the overall vulnerability management program.
Why Vulnerability Management Solutions are Important
Implementing effective vulnerability management solutions offers numerous benefits to organizations:
- Reduced Risk of Data Breaches: By identifying and addressing vulnerabilities before they can be exploited, organizations can significantly reduce their risk of data breaches and other security incidents.
- Improved Compliance: Many regulatory frameworks, such as GDPR, HIPAA, and PCI DSS, require organizations to implement vulnerability management programs. Vulnerability management solutions can help organizations meet these compliance requirements.
- Enhanced Security Posture: By proactively identifying and addressing vulnerabilities, organizations can improve their overall security posture and protect their assets from cyber threats.
- Cost Savings: Preventing data breaches and other security incidents can save organizations significant amounts of money in the long run. The cost of a data breach can include fines, legal fees, reputational damage, and lost business.
- Improved Operational Efficiency: Automating the vulnerability management process can free up IT staff to focus on other important tasks.
Types of Vulnerability Management Solutions
There are several different types of vulnerability management solutions available, each with its own strengths and weaknesses. Some common types include:
- Vulnerability Scanners: These tools automatically scan systems, applications, and networks to identify known vulnerabilities. They typically use a database of known vulnerabilities and signatures to identify potential weaknesses.
- Penetration Testing Tools: These tools simulate real-world attacks to identify vulnerabilities that can be exploited by malicious actors. Penetration testing can be used to assess the effectiveness of security controls and identify weaknesses in systems and applications.
- Configuration Management Tools: These tools help organizations manage the configuration of their systems and applications to ensure that they are securely configured. They can be used to identify misconfigurations that could lead to vulnerabilities.
- Patch Management Tools: These tools help organizations manage the process of patching software to address known vulnerabilities. They can automate the process of downloading, testing, and deploying patches.
- Threat Intelligence Feeds: These feeds provide organizations with information about emerging threats and vulnerabilities. This information can be used to prioritize vulnerability remediation efforts and proactively protect against new threats.
Factors to Consider When Choosing Vulnerability Management Solutions
Choosing the right vulnerability management solutions for your organization can be a complex process. There are several factors to consider, including:
- Your Organization’s Size and Complexity: Larger and more complex organizations typically require more comprehensive vulnerability management solutions than smaller organizations.
- Your Industry and Regulatory Requirements: Organizations in highly regulated industries, such as healthcare and finance, may have specific vulnerability management requirements.
- Your Budget: Vulnerability management solutions can range in price from free to very expensive. It’s important to choose a solution that fits your budget.
- Your Technical Expertise: Some vulnerability management solutions are more complex to implement and manage than others. It’s important to choose a solution that your IT staff has the expertise to use effectively.
- Integration with Existing Security Tools: Choose vulnerability management solutions that integrate with your existing security tools, such as your SIEM system and your intrusion detection system. This will allow you to get a more comprehensive view of your security posture.
- Reporting Capabilities: The vulnerability management solutions should provide comprehensive reporting capabilities to track progress and identify trends.
- Support and Training: Ensure that the vendor provides adequate support and training to help you implement and manage the solution effectively.
Best Practices for Implementing Vulnerability Management Solutions
Implementing vulnerability management solutions is only the first step. To ensure that your vulnerability management program is effective, it’s important to follow these best practices:
- Develop a Vulnerability Management Policy: This policy should outline the scope of your vulnerability management program, the roles and responsibilities of different stakeholders, and the procedures for identifying, assessing, and remediating vulnerabilities.
- Prioritize Vulnerability Remediation: Not all vulnerabilities are created equal. It’s important to prioritize remediation efforts based on the severity of the vulnerability, the affected assets, and the likelihood of exploitation.
- Automate the Vulnerability Management Process: Automating the vulnerability management process can help you identify and address vulnerabilities more quickly and efficiently.
- Regularly Scan for Vulnerabilities: Regularly scan your systems, applications, and networks for vulnerabilities. The frequency of scanning should be based on the criticality of the assets and the threat landscape.
- Patch Software Promptly: Patch software promptly to address known vulnerabilities. Patching is one of the most effective ways to prevent exploitation of vulnerabilities.
- Monitor for New Threats: Monitor for new threats and vulnerabilities. This information can be used to prioritize vulnerability remediation efforts and proactively protect against new threats.
- Test Your Security Controls: Regularly test your security controls to ensure that they are effective. This can be done through penetration testing or other security assessments.
- Train Your Employees: Train your employees on security awareness and best practices. Employees are often the weakest link in the security chain.
- Review and Update Your Vulnerability Management Program: Regularly review and update your vulnerability management program to ensure that it remains effective in the face of evolving threats.
The Future of Vulnerability Management
The field of vulnerability management is constantly evolving. As cyber threats become more sophisticated, vulnerability management solutions will need to adapt to keep pace. Some trends that are shaping the future of vulnerability management include:
- Increased Automation: Automation will play an increasingly important role in vulnerability management. Automated scanning, assessment, and remediation tools will help organizations identify and address vulnerabilities more quickly and efficiently.
- Integration with Threat Intelligence: Vulnerability management solutions will increasingly integrate with threat intelligence feeds to provide organizations with real-time information about emerging threats and vulnerabilities.
- Cloud-Based Vulnerability Management: Cloud-based vulnerability management solutions will become more popular as organizations move their IT infrastructure to the cloud.
- Risk-Based Vulnerability Management: Organizations will increasingly adopt a risk-based approach to vulnerability management, focusing on the vulnerabilities that pose the greatest risk to their business.
- AI and Machine Learning: Artificial intelligence (AI) and machine learning will be used to improve the accuracy and efficiency of vulnerability scanning and assessment.
Conclusion
Vulnerability management solutions are an essential component of any organization’s security strategy. By understanding the different types of solutions available, the factors to consider when making your decision, and best practices for implementation and maintenance, you can choose the right solution for your organization and protect your assets from cyber threats. Remember to continually assess and adapt your vulnerability management program to stay ahead of the evolving threat landscape. Investing in robust vulnerability management solutions is an investment in the long-term security and resilience of your organization. [See also: Cybersecurity Best Practices for Small Businesses]
