Top Intrusion Detection Systems (IDS): Protecting Your Network in 2024
In today’s digital landscape, network security is paramount. Organizations face an ever-increasing barrage of cyber threats, making robust intrusion detection systems (IDS) essential for safeguarding sensitive data and maintaining operational integrity. An intrusion detection system (IDS) acts as a security guard for your network, monitoring network traffic for malicious activity and alerting administrators to potential threats. Selecting the right IDS is a critical decision, and this article explores the top IDS solutions available in 2024, helping you make an informed choice to protect your digital assets.
Understanding Intrusion Detection Systems
Before diving into the top IDS solutions, it’s crucial to understand what an IDS is and how it works. An IDS analyzes network traffic and system activity for suspicious patterns that may indicate a security breach or policy violation. Unlike intrusion prevention systems (IPS), which actively block malicious traffic, IDS primarily focuses on detection and alerting. However, many modern IDS solutions offer integrated IPS capabilities for a more comprehensive security posture.
Types of Intrusion Detection Systems
There are several types of intrusion detection systems, each with its strengths and weaknesses:
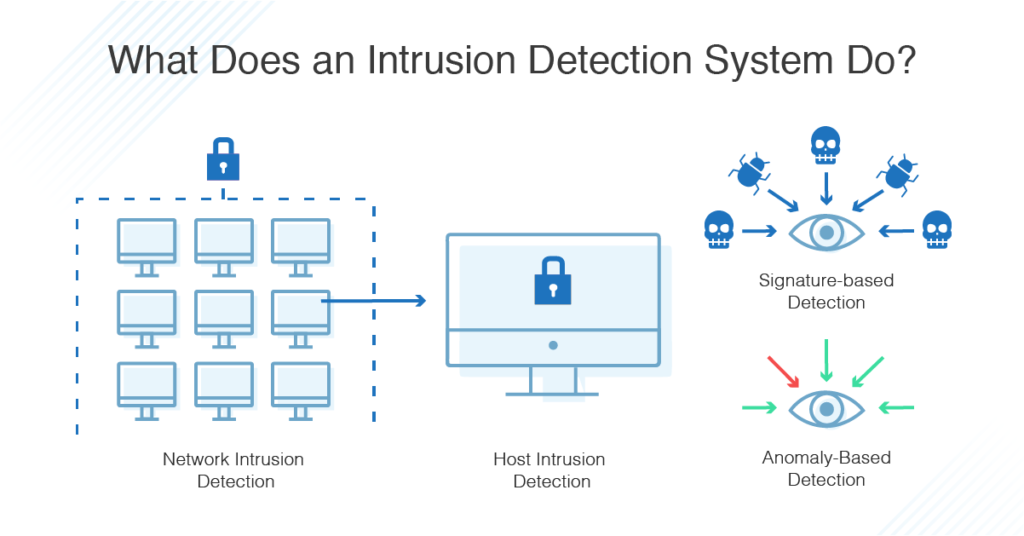
- Network Intrusion Detection Systems (NIDS): These systems monitor network traffic at strategic points within the network to detect suspicious activity. They analyze packets traversing the network, looking for patterns that match known attack signatures or anomalous behavior.
- Host-based Intrusion Detection Systems (HIDS): HIDS are installed on individual hosts or endpoints, such as servers or workstations. They monitor system logs, file integrity, and other host-specific activities to detect malicious activity.
- Signature-based Intrusion Detection Systems: These systems rely on a database of known attack signatures to identify malicious activity. When network traffic or system activity matches a signature, the IDS generates an alert.
- Anomaly-based Intrusion Detection Systems: Anomaly-based IDS establish a baseline of normal network or system behavior and then detect deviations from that baseline. This approach can identify novel attacks that are not yet known to signature-based systems.
- Hybrid Intrusion Detection Systems: These systems combine multiple detection methods, such as signature-based and anomaly-based detection, to provide a more comprehensive security solution.
Key Features to Look for in an IDS
When evaluating intrusion detection systems, consider the following key features:
- Detection Accuracy: The IDS should be able to accurately detect malicious activity with minimal false positives and false negatives.
- Real-time Monitoring: Real-time monitoring allows for immediate detection and response to threats.
- Comprehensive Coverage: The IDS should provide coverage for a wide range of attack vectors and protocols.
- Scalability: The IDS should be able to scale to meet the growing needs of your organization.
- Ease of Use: The IDS should be easy to deploy, configure, and manage.
- Reporting and Analytics: The IDS should provide detailed reports and analytics to help you understand security trends and identify potential vulnerabilities.
- Integration: The IDS should integrate with other security tools, such as firewalls and SIEM systems, to provide a more comprehensive security solution.
Top IDS Solutions in 2024
Here are some of the top intrusion detection systems available in 2024:
Snort
Snort is a widely used open-source IDS that has been around for over two decades. It is a powerful and flexible IDS that can be used to detect a wide range of threats. Snort uses a rule-based language to define attack signatures and can be configured to generate alerts based on various criteria. It’s a solid choice for budget-conscious organizations with skilled security personnel.
Pros:
- Open-source and free to use
- Large and active community
- Highly customizable
- Extensive rule set
Cons:
- Can be complex to configure and manage
- Requires technical expertise
- May generate false positives
Suricata
Suricata is another popular open-source IDS that is known for its high performance and scalability. It is a multi-threaded IDS that can handle high volumes of network traffic. Suricata also supports a wide range of protocols and attack signatures. It is often compared to Snort and is considered a strong alternative.
Pros:
- Open-source and free to use
- High performance and scalability
- Multi-threaded architecture
- Supports a wide range of protocols
Cons:
- Can be complex to configure and manage
- Requires technical expertise
- May generate false positives
Zeek (formerly Bro)
Zeek, formerly known as Bro, is a powerful network security monitoring framework that goes beyond traditional IDS functionality. It provides deep packet inspection and analysis, allowing you to gain insights into network traffic and identify suspicious behavior. Zeek is often used for incident response and threat hunting.
Pros:
- Open-source and free to use
- Deep packet inspection and analysis
- Powerful scripting language
- Ideal for incident response and threat hunting
Cons:
- Steep learning curve
- Requires significant technical expertise
- Can be resource-intensive
Cisco Secure Intrusion Detection System (formerly Sourcefire)
Cisco Secure IDS, formerly Sourcefire, is a commercial IDS that offers a comprehensive set of features, including real-time threat detection, intrusion prevention, and malware protection. It integrates with other Cisco security products to provide a holistic security solution. Cisco Secure IDS is suitable for larger organizations that require enterprise-grade security.
Pros:
- Comprehensive feature set
- Real-time threat detection and prevention
- Malware protection
- Integration with other Cisco security products
Cons:
- Commercial product with associated costs
- Can be complex to deploy and manage
- May require Cisco expertise
IBM Security QRadar Network Security
IBM Security QRadar Network Security is a network intrusion detection system that provides real-time threat detection, vulnerability management, and security intelligence. It uses machine learning and behavioral analytics to identify suspicious activity and prioritize security alerts. QRadar is designed for large enterprises with complex security requirements.
Pros:
- Real-time threat detection
- Vulnerability management
- Security intelligence
- Machine learning and behavioral analytics
Cons:
- Commercial product with associated costs
- Can be complex to deploy and manage
- Requires specialized expertise
Trend Micro TippingPoint
Trend Micro TippingPoint is a network security platform that includes intrusion prevention, advanced threat protection, and vulnerability management. It uses a variety of techniques, including signature-based detection, anomaly detection, and machine learning, to identify and block malicious traffic. TippingPoint is suitable for organizations of all sizes that require comprehensive network security.
Pros:
- Comprehensive network security platform
- Intrusion prevention
- Advanced threat protection
- Vulnerability management
Cons:
- Commercial product with associated costs
- Can be complex to deploy and manage
Choosing the Right IDS
Selecting the right IDS for your organization depends on several factors, including your budget, technical expertise, security requirements, and the size and complexity of your network. Consider your specific needs and priorities when evaluating different IDS solutions. Organizations should prioritize an IDS that has the ability to adapt to new and emerging threats.
For organizations with limited budgets and technical expertise, open-source solutions like Snort and Suricata may be a good starting point. These IDS offer a high degree of customization and flexibility, but they require significant technical expertise to configure and manage. [See also: Open Source Security Tools]
For larger organizations with more complex security requirements, commercial IDS solutions like Cisco Secure IDS and IBM Security QRadar Network Security may be a better fit. These IDS offer a more comprehensive set of features and are typically easier to deploy and manage, but they come with associated costs. [See also: Enterprise Security Solutions]
Ultimately, the best IDS is the one that meets your specific needs and provides the level of security you require. It’s important to conduct thorough research and testing before making a final decision. Remember that an IDS is just one component of a comprehensive security strategy. It should be used in conjunction with other security tools and best practices to provide a layered defense against cyber threats.
Conclusion
Intrusion detection systems are a critical component of any organization’s security posture. By monitoring network traffic and system activity for malicious activity, IDS can help you detect and respond to threats before they cause significant damage. Choosing the right IDS is a crucial decision, and this article has provided an overview of some of the top IDS solutions available in 2024. Consider your specific needs and priorities when evaluating different IDS solutions and remember that an IDS is just one component of a comprehensive security strategy. By implementing a layered defense approach, you can significantly reduce your risk of a successful cyberattack.
