Evil Twin Network: Understanding and Protecting Yourself from This Wi-Fi Threat
In today’s hyper-connected world, Wi-Fi has become an essential utility, as vital as electricity or running water. We rely on it for work, entertainment, and staying connected with loved ones. However, this reliance also opens us up to various security threats, one of the most insidious being the evil twin network. An evil twin network is a rogue Wi-Fi access point that appears legitimate but is actually designed to steal your personal information. Understanding how these networks operate and how to protect yourself is crucial in maintaining your online security. This article will delve into the mechanics of the evil twin network, how to identify them, and the steps you can take to safeguard your data.
What is an Evil Twin Network?
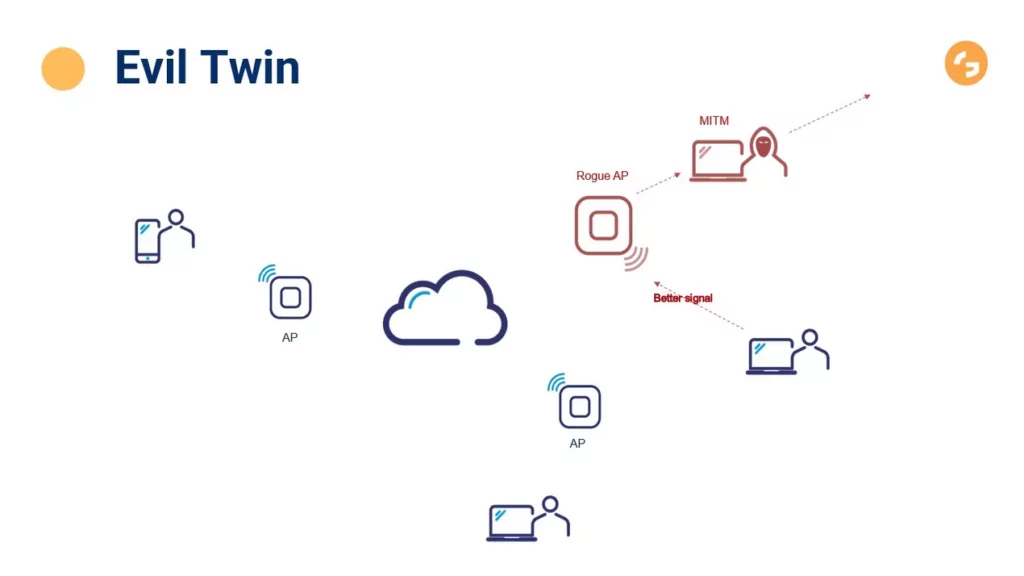
An evil twin network is essentially a fake Wi-Fi hotspot that mimics a legitimate one. Cybercriminals set up these evil twin networks in public places like coffee shops, airports, and hotels, where people are likely to connect to free Wi-Fi. The evil twin often uses a name similar to the legitimate network, such as “Starbucks Wi-Fi” or “Airport Free Wi-Fi,” making it easy for unsuspecting users to connect. Once you connect to the evil twin, the attacker can intercept your traffic, steal your login credentials, and even inject malware into your device. This is because all your network traffic is routed through the attacker’s server, giving them complete control over your online activity.
How Evil Twin Networks Work
The technical operation of an evil twin network is relatively straightforward. Here’s a breakdown of the process:
- Setup: The attacker sets up a Wi-Fi access point using a laptop or a dedicated device. They configure the network name (SSID) to resemble a legitimate hotspot.
- Enticement: The evil twin network broadcasts a strong Wi-Fi signal, often stronger than the legitimate network, to entice users to connect.
- Connection: When a user connects to the evil twin, they are often presented with a login page that looks authentic. This page may ask for credentials or personal information.
- Interception: Once connected, all the user’s network traffic passes through the attacker’s device. This allows the attacker to intercept usernames, passwords, credit card numbers, and other sensitive data.
- Redirection: The attacker can redirect the user to a legitimate website after capturing their information, making the attack less noticeable. They might also inject malware into the user’s device during this process.
Identifying an Evil Twin Network
Detecting an evil twin network can be challenging, but there are several clues to look out for:
- Check the Network Name (SSID): Verify the exact name of the Wi-Fi network with the establishment. A slight variation can indicate an evil twin. For instance, “Starbucks Wi-Fi” instead of “Starbucks.”
- Look for Missing Security Protocols: Legitimate networks usually have security protocols like WPA2 or WPA3. If a network is open and unsecured, it could be an evil twin.
- Beware of Suspicious Login Pages: If you are prompted to enter personal information on a login page that doesn’t seem legitimate, be cautious. Always check the URL and look for the HTTPS protocol, which indicates a secure connection.
- Monitor Network Performance: If your internet speed is significantly slower than expected, it could be a sign that you are connected to an evil twin network.
- Use a Wi-Fi Analyzer App: These apps can help you identify the signal strength, security protocols, and other details of nearby Wi-Fi networks, making it easier to spot anomalies.
Protecting Yourself from Evil Twin Attacks
Protecting yourself from evil twin attacks requires a combination of vigilance and proactive security measures. Here are some steps you can take:
Use a Virtual Private Network (VPN)
A VPN encrypts your internet traffic, making it unreadable to attackers. Even if you connect to an evil twin network, your data remains protected. [See also: Choosing the Right VPN for Your Needs]
Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security to your accounts. Even if an attacker steals your password, they will still need a second factor, such as a code from your phone, to access your account.
Be Wary of Open Wi-Fi Networks
Avoid connecting to open Wi-Fi networks unless absolutely necessary. If you must use them, only visit websites that use HTTPS and avoid entering sensitive information.
Keep Your Software Up to Date
Regularly update your operating system, web browser, and antivirus software. These updates often include security patches that protect against the latest threats. [See also: The Importance of Regular Software Updates]
Disable Auto-Connect to Wi-Fi
Prevent your device from automatically connecting to Wi-Fi networks. This will give you more control over which networks you connect to and reduce the risk of accidentally connecting to an evil twin network.
Verify Network Security Settings
Always check the security settings of the Wi-Fi network before connecting. Look for WPA2 or WPA3 encryption. If a network doesn’t have these, it’s best to avoid it.
Use a Dedicated Security App
Consider using a dedicated security app that can detect and block malicious Wi-Fi networks. These apps often use advanced techniques to identify evil twin networks and other threats.
Educate Yourself and Others
Stay informed about the latest security threats and share your knowledge with others. The more people are aware of evil twin networks, the less effective these attacks will be.
Real-World Examples of Evil Twin Attacks
Evil twin attacks are not just theoretical threats; they have been used in real-world scenarios with significant consequences. For instance, during political conventions, attackers have set up evil twin networks to intercept the communications of journalists and delegates. In other cases, attackers have targeted businesses by setting up fake Wi-Fi networks in their vicinity to steal customer data. These examples highlight the importance of being vigilant and taking proactive security measures.
The Future of Evil Twin Networks
As technology evolves, so do the tactics of cybercriminals. Evil twin networks are likely to become more sophisticated in the future, making them even harder to detect. Attackers may use advanced techniques such as machine learning to create more convincing fake networks and evade detection. Therefore, it’s crucial to stay ahead of the curve by adopting the latest security measures and staying informed about emerging threats.
Conclusion
The evil twin network is a serious threat to your online security. By understanding how these networks operate and taking proactive steps to protect yourself, you can significantly reduce your risk of becoming a victim. Remember to use a VPN, enable two-factor authentication, be wary of open Wi-Fi networks, and keep your software up to date. Staying vigilant and informed is the best defense against evil twin attacks. Protecting yourself in the digital world is a continuous process, and being aware of threats like the evil twin network is a crucial part of that process. Always verify the legitimacy of Wi-Fi networks before connecting and prioritize your online security. By doing so, you can navigate the digital landscape with confidence and peace of mind.
